Original author: Fu Shaoqing, SatoshiLab, All Things Island BTC Studio
V1.5 version modification notes:
(1) An article summarizing the basic knowledge system V1.0 of the construction of Bitcoins second layer (Layer 2) was published in February 2024. After writing in March Observing Bitcoins second layer from the perspective of a state machine, we can get More Thoughts and Conclusions article, we got some summary of the characteristics of different second layers. It will be easier to read if we summarize it into the basic knowledge system, so we released the V1.5 version.
(2) Modified the text expression content of some details, such as the connection technology between the first layer and the second layer.
(3) Because there are often disputes, the three concepts of Centralized, Decentralized, and Distributed in Section 2.4 are explained in more detail.
(4) The second picture in Section 2.4 has been improved and modified to make the contrast clearer.
(5) Added Section 2.5 to summarize the basic characteristics of blockchain and the characteristics of three Layer 2 constructions, making it easier to understand if multiple combination structures are used.
The rise of Bitcoin Inscription has brought new vitality to the Bitcoin ecosystem, causing more people to start paying attention to Bitcoin again. Some people say that it has opened the Pandoras box of the Bitcoin ecosystem. Among the many technical developments in the Bitcoin ecosystem, the construction of the second layer of Bitcoin is the top priority. In this direction, I drew on some well-known articles on the Internet, exchanges with many friends, and our team’s experience in the design and development of Web3 products, and summarized an article on the basic knowledge of the second layer of Bitcoin. This method is easy to summarize and learn, and because of the limitations of individual cognition, I hope it can attract more people to improve related ideas and allow this field to develop better.
The world of blockchain starts with Bitcoin and ends with the Bitcoin ecosystem.(I personally agree with the summary of Mr. Dashan from Waterdrop Capital.) Ethereum is also a side-chain technology exploration of Bitcoin. In this article, we will use second-layer construction or second-layer network construction interchangeably. Usually, the term second-layer network construction is relatively narrow, and second-layer construction is a broader concept. However, in order to adapt to the common explanations such as layer 1 network and layer 2 network that are usually discussed in the industry, we will also use the concept of layer 2 network construction. These two words are the same concept in this article.
1. Common tasks to be accomplished by Layer 2
In order to understand the basic problems that need to be solved in the second-layer construction of Bitcoin. Let’s start by understanding the basic characteristics of the blockchain system.
1.1. Basic characteristics and basic requirements of blockchain
This article uses a concept proposed by Vitalik: the blockchain is a world computer. It will be clearer for us to understand the various characteristics of blockchain from this perspective. In later chapters, we will also analyze the possibility of the development of this world computer based on the von Neumann structure in computers.
Let’s first summarize some basic features:
Note:
The demand generated to maintain the normal operation of the world computer of the blockchain is called internal demand;
To satisfy the needs of users using this world computer is called external demand.
Open and transparent:This is the data storage and instruction execution characteristics of the world computer of the blockchain. It is also an internal demand characteristic that requires many distributed nodes around the world to participate in calculations. This feature just satisfies the users right to know the data, and is the result of the internal collaboration requirements of the world computer itself and the external needs of the user. The privacy features mentioned later are to meet the external needs of users without destroying the collaboration requirements of the world computer itself. Decentralization: This feature is an architectural feature of this world computer. The degree of decentralization and fault tolerance are theoretically determined by the Byzantine Generals Theory (the possibility of dishonesty among collaborators, that is, failure to comply with the agreement) situation) is supported. Non-Byzantine general systems are not blockchain systems in theory. We will see two situations of non-blockchain systems in second-layer construction later. The degree of decentralization is an important indicator of blockchain security and is the basis for certain features.
safety:Security is a combination of internal requirements arising from the architectural characteristics of this world computer and external requirements required by users. From the micro level, security is guaranteed by cryptography-related technologies, and from the macro level, it is ensured by the decentralization of the architecture, so that this world computer will not be affected by the forgery of micro data or the destruction of the macro architecture. security.
Calculate ability:One of the main functions of the blockchain, the world computer, is computing power. To measure this indicator, we generally use it to examine whether it is Turing complete. In order to maintain their main characteristics, some chains are deliberately designed to be Turing incomplete. For example, in the Bitcoin network, Satoshi Nakamoto not only made its code instructions not Turing-complete, but also deliberately deleted some instruction sets during development to maintain its stability and security. All Turing complete technologies are designed to expand the computing power of the blockchain. From the perspective of layered design, simple systems are more suitable for the bottom layer.
performance:With the same computing power, performance is another major capability when examining computers in the world of blockchain. It is generally measured by TPS, which is the number of transactions processed per second.
storage:Blockchain is described as a world computer, so it must have a storage function, which is the ability to record data. At present, it is basically stored in the block, and more professional on-chain storage outside the block is still under development.
privacy:Privacy is a subdivided requirement in the World Computer, which requires that the permissions of data producers and users be maintained during the calculation and storage process (we also put censorship resistance in the privacy part). This is basically driven by the external needs of users.
There is also a comprehensive indicator, scalability, which generally refers to the scalability of the entire architecture. This feature affects most basic features. At the architectural level, the scalability of the system is a very important indicator. There will also be some other connection capabilities, or other capabilities for specific scenarios. I will not discuss them too much here. I will analyze them in detail when encountering these special scenarios.
Among the basic characteristics of these blockchains, most of them are restricted by impossible triangles. For example, the DSS conjectures are decentralization (Decentralization, D), security (Security, S) and scalability (Scalability, S). As shown below:
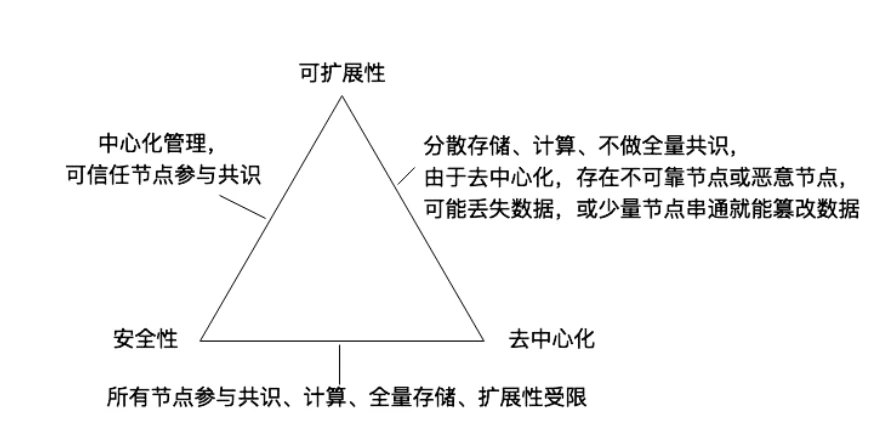
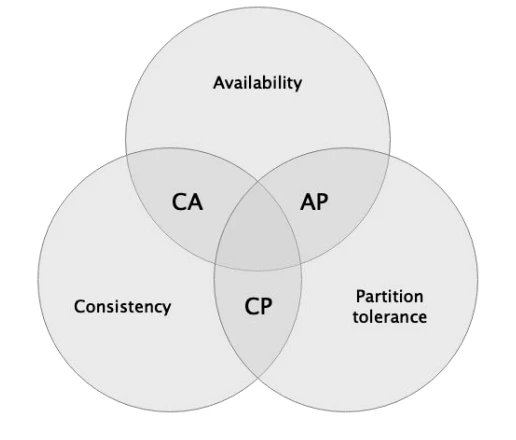
In distributed systems, a similar impossible triangle is the CAP principle. CAP refers to the fact that Consistency, Availability, and Partition tolerance cannot be achieved simultaneously in a distributed system. The blockchain system is a distributed system with Byzantine Generals Problem, so it also applies to the CAP principle.
The CAP principle is shown in the figure below:
1.2. The role of second-story construction
What roles are to be fulfilled in the second floor construction? What functions are provided? The second-floor construction must expand the deficiencies of the first-floor system. Things that are not suitable to be completed on the first-floor system can be completed on the second-floor construction.
We can draw a preliminary conclusion from the blockchain features summarized above, which must be to expand these basic capabilities:Openness and transparency, decentralization, security, computing power, performance (throughput), storage, privacy, etc.. In addition to these basic capabilities from a technical perspective, there is also a very important economic issue that needs to be solved, which is cost reduction. Usually the overall cost of executing transactions on a one-tier network is relatively high, and a two-tier network needs to be used to reduce these costs.
To sum it up in one sentence is toIncrease capacity, reduce costs, customize featuresThe three-dimensional plans are all two-story construction. As for the customization features, they are not obvious enough yet, or are often buried in the first two features and are somewhat confusing. We can understand that the characteristics of the first-layer network are required to different extents for many applications, and the implementation of various characteristics can be readjusted for certain applications on the second layer.
In the second-layer construction, the basic capabilities of the blockchain will have trade-offs, and some features will be reduced or even discarded in exchange for significant improvements in certain features. For example: in order to improve performance, some second layers will reduce the degree of decentralization and reduce security; in order to increase throughput, some second layers, such as the Lightning Network, will change the system structure and settlement method. There are also some that enhance certain features without reducing the basic features, such as the RGB processing method, which obviously increases privacy and censorship resistance, but increases the difficulty of technical implementation. In later cases, we will see two-story construction that simultaneously reduces or alters several properties.
Among them, cost reduction should be a basic need for all second-story construction. (Are there any second floors that don’t reduce costs? I haven’t seen one yet.)
1.3. Why layered design?
Layered design is a means and methodology for humans to deal with complex systems. It achieves the modularity, maintainability and scalability of the system by dividing the system into multiple hierarchical structures and defining the relationships and functions between each layer. Thereby improving the design efficiency and reliability of the system.
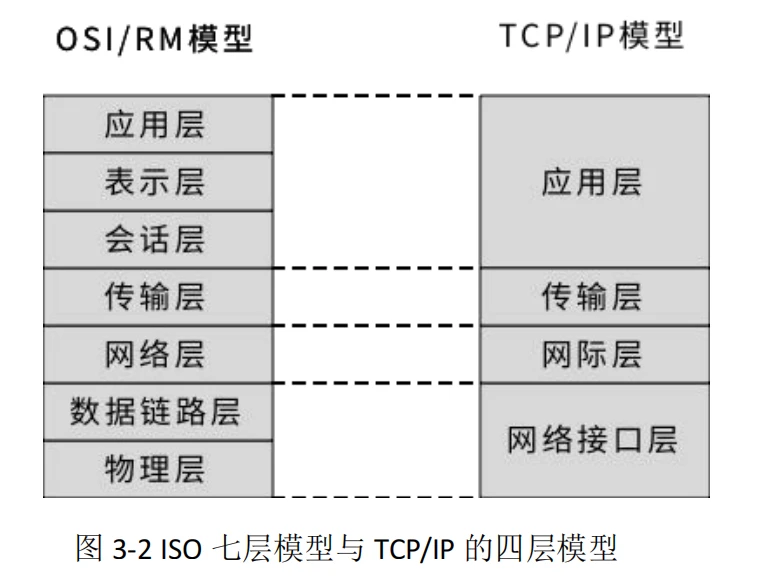
For a broad and large protocol system, there are obvious benefits to using layering. This makes it easy for people to understand, easy to implement by division of labor, and easy to improve by modules. Such as the ISO/OSI seven-layer model design in computer networks, but in specific implementation, some layers can be combined. For example, the specific network protocol TCP/IP is a four-layer protocol. As shown below:
Specifically, the advantages of protocol layering:
Each level is independent.A certain layer does not need to know how the layer below it is implemented, but only needs to know the services provided by this layer through the interface between layers. In this way, the complexity of the entire problem is reduced. In other words, how the work of the upper layer is performed does not affect the work of the next layer. In this way, as long as the interface remains unchanged when designing the work of each layer, we can adjust the working methods within the layer at will.
Good flexibility.When any layer changes, as long as the interface relationship between layers remains unchanged, the layers above or below this layer will not be affected. When there is a technological innovation in a certain layer or a problem occurs in the work of a certain layer, it will not affect the work of other layers. When troubleshooting, only the problems of this layer alone need to be considered.
Structurally separable.Each layer can be implemented using the most appropriate technology. The development of technology is often asymmetrical, and hierarchical division effectively avoids the barrel effect, and the overall work efficiency will not be affected by imperfect technology in one aspect.
Easy to implement and maintain.This structure makes implementing and debugging a large and complex system easier to handle because the entire system has been decomposed into several relatively independent subsystems. When debugging and maintaining, each layer can be debugged independently to avoid the situation of not finding or solving the wrong problem.
Can promote standardization work.Because the functions of each layer and the services they provide have been accurately described. The advantage of standardization is that one of the layers can be replaced at will, which is very convenient for use and research.
The hierarchical modular design idea is a common method in the technical field for dealing with a project that has a huge function and requires the cooperation of many people and continuous improvement of engineering projects. It is an effective method that has been tested in practice.
2. Several construction ideas for Bitcoin Layer 2
We take the second-layer construction of Bitcoin as a case to conduct relevant analysis. There are three obvious second-layer construction routes for Bitcoin’s second layer:
(1) One is a chain-based expansion route, which is very similar to the second layer of EVM and is a blockchain structure;
(2) One is based on a distributed route, represented by the Lightning Network, which is a distributed structure.
(3) There is also a route based on a centralized system, represented by a centralized index, which is a centralized structure.
The first two methods are very distinctive, and there are already some products in use and products under exploration. For the first method, due to the booming development of Ethereum and the exploration of other Bitcoin imitation chains, chain-based second-layer expansion is relatively easier, and there are more reference cases. The second distributed method is usually more difficult and develops slower, represented by the Lightning Network. The third method is very controversial because it does not look like a two-story building, but it seems to complete the function of a two-story building.
Which two-story construction plan is better? We use a market test result as a measurement indicator. Whichever second-tier network has a higher TVL (Total Value Locked), that plan is the optimal plan. With the development of time and technology, this optimal solution will be a process of change.
As for the definition of Bitcoin’s second-tier network, as long as it relies on the Bitcoin network, establishes a technical connection with the Bitcoin network, and has some features that are better than Bitcoin’s first-tier network, it is considered Bitcoin’s second-tier network construction. In other words, as long as BTC is consumed as gas, a system that uses BTC as the underlying asset and expands the performance of Bitcoin is considered a second-tier construction. Based on this judgment, we should recognize the third type of second-tier network construction, that is, the second-tier construction of a centralized structure.
The development of Bitcoins own technology, such as modified OP_RETURN, SegWit (isolated witness), Taproot (isolated witness upgraded version), Schnnor signature, MAST, and Tapscript should all be designed for the purpose of connecting the first and second layers, and these technologies should not be used There are too many development functions, because no matter how much the first-tier network is expanded, there will be no qualitative breakthrough, and second-tier construction must be carried out. However, in the absence of better-used second-layer Bitcoin products, these technical capabilities that connect the first and second layers will be overused for a period of time.
2.1. Chain-based second-layer construction
Early Bitcoin imitation chains made various explorations, such as Colorcoin (colored coins), CovertCoins and MasterCoin; various expanded Bitcoin imitation chains, such as BCH (Bitcoin Cash), BSV (Bitcoin SV) , 5 BTG (Bitcoin Gold); Various side chain technologies are based on chain expansion construction cases, which can be said to be a second layer in a broad sense.
Including Ethereum, which is also an exploration of improvements based on Bitcoin. After convincing other project teams to no avail, Vitalik formed his own team to publish a white paper and develop a new generation of blockchain in view of the imperfections of Bitcoin: UTXOs accountless system, non-Turing completeness of the execution language, poor scalability and other issues. Blockchain system. Although this kind of exploration of Ethereum is not a direct second-layer construction on Bitcoin, it is a kind of chain-based construction exploration in a broad sense.
Ethereum’s exploration of improvements to Bitcoin’s imperfections, as well as the development and verification of the second layer on Ethereum, provide a reference case for the development of chain-based second layer networks on Bitcoin. Various Rollup solutions, cross-chain solutions, message channel technology, and Ethereum’s own sharding technology(From the perspective of the hierarchical thinking of dealing with complex systems, perhaps this idea of solving multiple problems at one level is wrong), making the Ethereum technology ecosystem flourish, many people once thought that the development direction and future of the public chain had been determined, and the ecology represented by Ethereum had won. In fact, this is also a manifestation of the relative maturity of the second-layer construction based on the chain. However, chain-based second-layer construction is only one method of second-layer construction. It has its own advantages and disadvantages, and other second-layer technologies are also needed to improve the entire second-layer ecology.
The chain-based second-layer construction in Bitcoin roughly includes two typical chain types, one is an EVM-compatible account model, and the other is a Bitcoin-like UTXO model. Existing cases (we use the generalized second-layer definition) include: Ethereum, Polygon, Bsc, Arbitrum, etc. are all EVM account models, and CKB (Nervos) and Chia are all UTXO models.
In the following chapters, some cases will be introduced in more detail when introducing the Bitcoin second-layer projects that have been implemented.
In addition, second-layer projects that have been successful on Ethereum will also be added to the chain-based second-layer construction of Bitcoin. For these second-layer projects on Ethereum, the workload and challenges of transforming into the second layer on Bitcoin will be less. Based on the development and theoretical achievements of Ethereums rollup maturity and modularity, this method of second-layer construction will become the mainstream of expansion discussions and is also the fastest-effective solution.
How successful will this transformation be? Developmental testing remains. We can make some preliminary judgments from the advantages and disadvantages of this chain-based second-layer construction.
What are the advantages and disadvantages of chain-based second-layer construction?
The disadvantage of this solution is that the second layer based on the chain is generally limited by the limitations of the blockchain, and the performance improvement is limited. Either the system becomes more centralized, or the block generation interval is reduced, and the block capacity is increased. , the safety will generally be reduced. As a result, a two-story building above the second floor was born, which is also called Layer 3 or Layer 4.
The advantage is that this solution maintains most of the basic characteristics of the blockchain, and generally solves the Turing-complete problem. The transaction costs are also significantly reduced, and it expands the capabilities of the first-layer network to a certain extent. Moreover, this solution has abundant construction cases, and the technical implementation is relatively easy. There are already many exploration cases, and the migration of upper-layer applications is also very convenient. It is a faster implementation method. I believe that this method will produce more second-hand solutions. layer network.
Roughly speaking, due to the expansion limitations of this method, there should be many projects on the second floor based on the chain structure. There may be one or more second floors in each vertical field. Each project must complete its own unique second floor construction. , to meet the needs of certain applications. Its value will also be determined by the number and total value of applications on it.
2.2. Second-layer construction based on distributed system
In the second-tier construction, there are also some constructions based on distributed systems. In this solution, the second-layer structure and framework are no longer blockchain structures, but a distributed system based on Channel. Lightning Network is a typical representative.
A distributed system consists of a limited set of processes and a limited set of channels. In order to deliver messages in a distributed system, the data, events, and channels that need to be controlled are already a relatively complex set of problems. The Channel we refer to here is the upper-level channel concept, such as the payment channel in the Lightning Network and the message channel in Nostr, rather than the underlying concept of the specific technology Channel in the distributed network.
There are two categories in the second-layer construction of distributed systems:
(1) Only value transfer is completed, similar to the Lightning Network;
(2) Not only complete value transfer, but also complete Turing-complete technology, such as RGB;
In the distributed two-layer construction solution, because it is value transmission, there are many difficulties that exceed the original message transmission. For example, the total value capacity in the channel, the rigor of transactions, and the inability to consume twice are all beyond message transmission. difficulty. Therefore, the development of distributed second-tier construction is not as fast as that of chain-based second-tier construction, and there are not many mature cases.
If you want to complete Turing-complete calculations on such a second layer, that is, build a Turing-complete virtual machine system on Channel, it will be even more difficult. Like the RGB protocol, it implements Turing-complete calculations on a distributed system through client verification and one-time sealing.
Regarding the second-layer construction of distributed distributed systems in Bitcoin, existing cases include: Lightning Network, RGB, are there any more famous cases? If we look at it according to the standard of generalized two-tier construction, does Nostr also belong to the second-tier construction of distributed systems with Channel mechanism? When sorting out Ethereum information, I saw cases of using Channels in Ethereum documents: Connext, Raiden, and Perun, which can be used as exploration directions for in-depth researchers.
In the following chapters, the already running Bitcoin second-layer project will be introduced, and the Lightning Network and RGB will be introduced in more detail.
What are the advantages and disadvantages of distributed systems based on distributed systems?
The advantages of this solution are generally that the system is more decentralized, the second-layer network can accommodate countless nodes, has better privacy and censorship resistance, and has unlimited scalability, so that theoretically the performance becomes extremely high.
The disadvantage of this solution is that the technical implementation is complex, and the routing algorithm, value splitting and encapsulation algorithms in a huge distributed system are relatively complex. Compared with information transfer, there is still a lack of engineering implementation experience and infrastructure in value transfer. This is also one of the reasons why the Lightning Network has been considered to be developing slowly.
In addition, it is a very big challenge to implement a Turing-complete system in this kind of system, that is, Channel+ computing. It can definitely be realized in theory, but in practice it is still in the early experimental stage. RGB is a typical representative of this situation.
Once a breakthrough is achieved in the second-layer construction based on distributed methods, it will greatly promote the development of upper-layer applications. The decentralization capabilities formed by its huge distributed nodes and the Turing-complete code execution capabilities will better support the next generation of Internet applications, which is the Mass Adoption scenario everyone is talking about.
It can be roughly judged that the second layer of the distributed structure based on Channel generally only has a few parallel projects. There are two main reasons. One is the unlimited expansion capability of this system, and the other is the technical difficulty of implementation. Therefore, such a system needs to be more open in design and concept, and can accommodate more people and teams to participate. And based on this second-layer infrastructure application development team will also promote the development of this second-layer, for example, the RGB-based BiHelix project.
2.3. Second-layer construction based on centralized system
Do you want this category? There should be controversy.
Centralized index structures like Ordinals, or indexers of certain functional nodes are all centralized structures, and they are also a two-layer construction idea. However, this construction idea will be less recognized because the second layer is too centralized and the expansion of the first layer network is very limited. In the second-layer construction of this centralized structure, the basic characteristics of various blockchains depend on the first-layer network. The second layer only serves as some simple calculation and statistical functions. The second layer sometimes seems to be a dispensable The temporary existence can be replaced by another second floor at any time, and its importance does not seem to be that high. But from the perspective of On-Chain and Off-Chain, and from the perspective of improving the capabilities of the first-layer network, this centralized structure is also a second-layer extension.
In addition to Ordinals, examples of such systems should include centralized exchanges. Projects in this situation will not be introduced in the following cases.
Advantages and disadvantages of two-story construction based on a centralized system:
The advantage is that the centralized system is very mature, has countless available cases and optimization solutions, is completely Turing complete and has excellent performance.
The disadvantage is that the second layer is extremely centralized, and all the basic features of the blockchain depend on the first layer network.
Roughly speaking, there should be fewer projects on the second floor based on a centralized structure, or even a phased existence. After the distributed structure based on chain structure and Channel matures and improves, most of the second-layer construction of centralized structures will disappear, or only a centralized second-layer with fewer characteristic scenarios will remain. At the current stage, because the centralized system is very mature, it can well meet the scenarios of On-Chain data and Off-Chain calculations when it can write data on the basic chain. It is the easiest to implement for primary applications in the current Bitcoin ecosystem. pattern, is used extensively.
2.4. Broader second-level concepts and higher-level applications
From the structural analysis of the two-story building above, there areBlockchain structure, distributed system structure, centralized system structure.This is our common classification of system structures: Centralized, Decentralized, Distributed. From this perspective, it is easier for us to understand the characteristics and applicable scenarios of each type. The three second-layer types all have their advantages and disadvantages. In the future complete Bitcoin ecosystem, all three types should be distributed according to different scenarios.
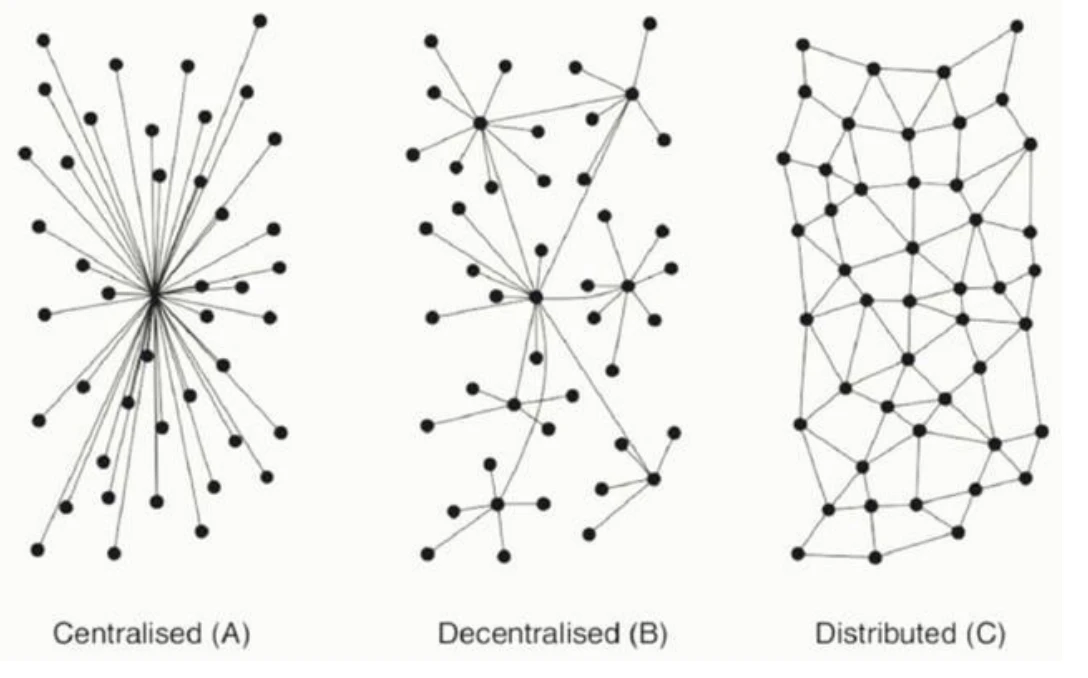
I used this diagram with reference to Vitaliks article: The Meaning of Decentralization, link URL:https://medium.com/@VitalikButerin/the-meaning-of-decentralization-a0c92b 76 a 274
There are often some disputes about this picture in China. It is believed that the Decentralized and Distributed picture logos are reversed. From the perspective of control and decision-making, we should be able to eliminate this controversy and better understand Decentralized and Distributed. Regarding Centralized (A) in the figure, there should be no dispute among everyone from various perspectives, so we only compare decentralized and distributed. Decentralized Decentralization is actually a kind of multi-centering, and its control and decision-making also require the participation of certain central nodes. At this time, control and decision-making are called consensus. For example, only full nodes with mining capabilities in Bitcoin have the ability to determine the generation of new blocks and the content written into new blocks. Those nodes without mining capabilities are read-only nodes or verification nodes. In POS and DPOS chains, this situation will be more obvious. Only the consensus node can decide what to generate and write in the new block. The difference between synchronous algorithms and asynchronous algorithms in consensus protocols is also more obvious, which will determine the number of nodes that can be accommodated in the blockchain network. In the distributed system, there is no obvious center at all, only nodes. Any node can join or leave the network at any time, and its control and decision-making are local. This is also one of the reasons why distributed systems can achieve very high performance. . Does this explanation eliminate the common disputes between Decentralized and Distributed?
In addition, the blockchain crowd often discusses Layer 3 or even Layer 4 above the second-layer construction, which is a generalized second-layer construction. Layer 3 and Layer 4 are completely different concepts from the 5-layer structure of the Web3 technology stack proposed by Gavin Wood. Layer 3 and Layer 4 in the Web3 technology stack are the classification methods of application protocols.
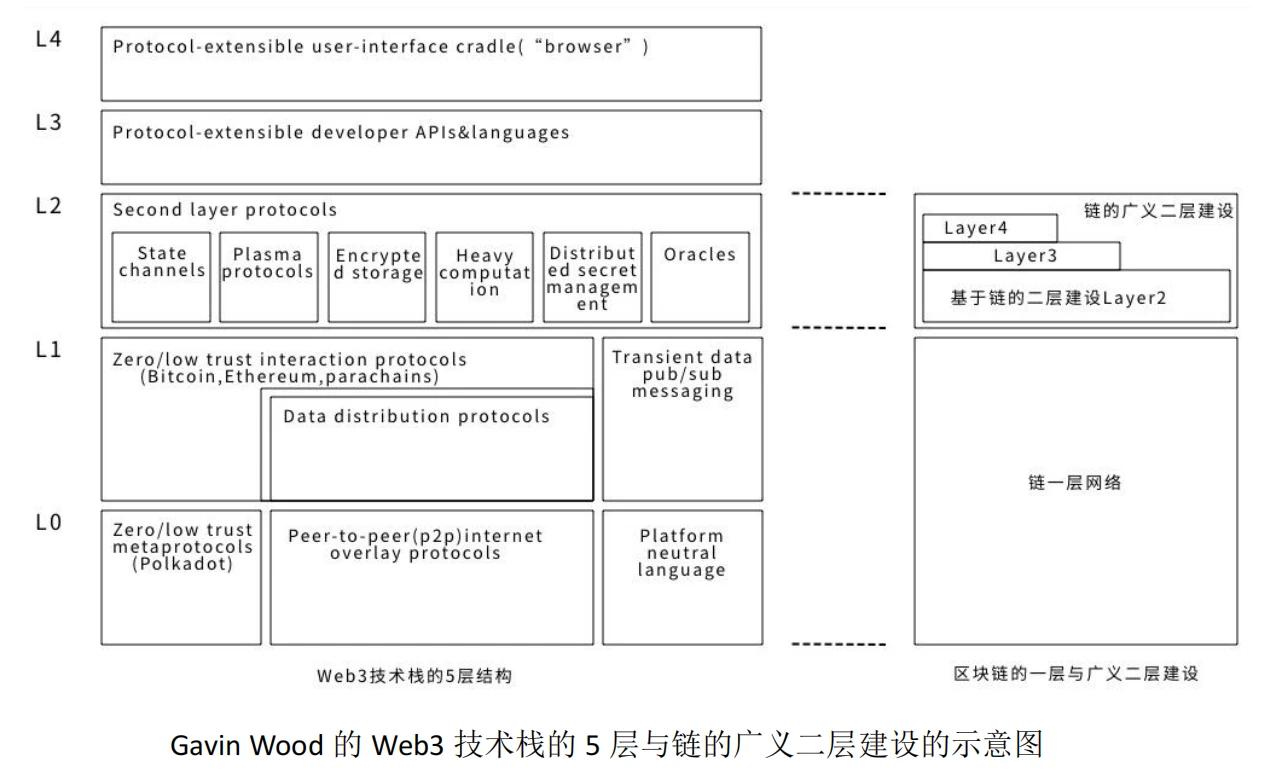
What impact will these second-story constructions have on upper-level applications? With the basic features provided by the blockchain system:Openness and transparency, decentralization, security, computing power, throughput, storage, privacy, etc., upper-layer applications will be built on these second-layer extensions, and will interact with each other on these second-layer applications. The second-layer expansion based on the blockchain structure, the second-layer expansion of the distributed structure, the second-layer expansion of the centralized structure, and some centralized applications will produce real, large-scale Web3.0 applications.
2.5. Summary of the basic characteristics of blockchain and the characteristics of three Layer 2 constructions
The content of this section comes from another article I wrote, Observing the second layer of Bitcoin from the perspective of a state machine, you can get more thoughts and conclusions. The summary table and some conclusions are directly quoted here. For the system architecture of Web3.0 applications, please also refer to that article.
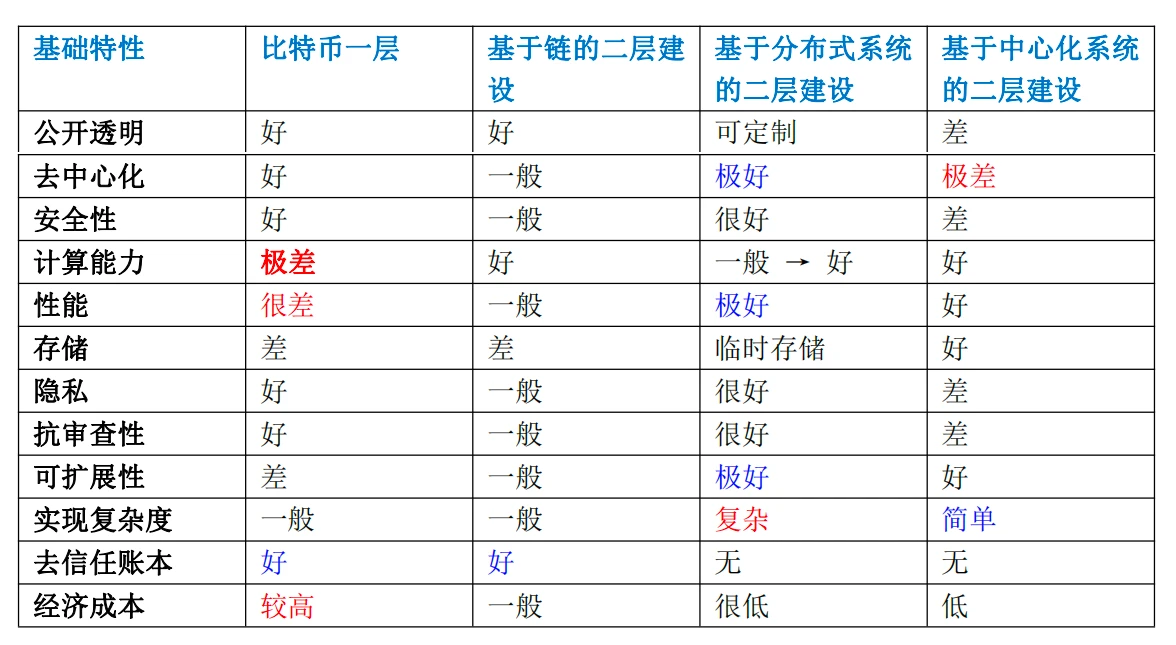
Through the above table, we can roughly summarize the characteristics of blockchain structure, distributed system structure, and centralized structure.
(1) Blockchain structure
The biggest benefit of the blockchain structure is that it solves trust-related issues (the role of the ledger) and can record the change process of data (state transition), so the data and calculation rules become trusted data and trusted calculations.
The biggest problem of the blockchain structure is poor performance. There are two reasons for this. First, the blockchain structure cannot remove partial calculation scenarios, and all requests are processed in a full calculation manner. For example, partial calculation and global calculation, local data and global data, temporary data and permanent data. Second, the blockchain structure has an obvious performance upper limit. If layer 2 expansion is performed through a chain, the number of supported transactions is also very limited.
In order to expand the performance of blockchain-containing structures, multi-layer construction is required and it needs to be used in conjunction with heterogeneous systems.
From the above table, only the blockchain structure can realize the trustless ledger function. Therefore, if a system wants to realize the trustless ledger function, it must include a blockchain system. However, due to the performance requirements of large-scale applications, the blockchain system must be combined with other systems to meet the needs.
(2) Distributed system
In the table above, we can see the obvious advantages of distributed systems:Decentralization, performance, scalabilityThey are all excellent, except for the more complicated features in function implementation. In addition, distributed systems do not have the ability to trust the ledger.
Therefore, if we can use the distributed system in the second-layer construction based on the first-layer ledger function of Bitcoin, we can theoretically achieve unlimited performance expansion while maintaining the basic characteristics of the blockchain. A case in this area is represented by Bitcoin + Lightning Network. The performance of this combination is Bitcoins 7 TPS * ∞.
The reason for achieving Turing completeness in a distributed system is that the cost of recording and running smart contracts in a blockchain system is very high because it is global data and global code. Therefore, smart contracts are also suitable for layered theory, which limits the code storage and execution of smart contracts to participants.
(3) Centralized system
In the above table, we can see that the benefit of the centralized system is that the engineering implementation is relatively simple. This is due to the simple internal logic control and simple calculation. Similarly, centralized systems do not have the ability to trust ledgers. The advantages of a centralized system are not outstanding. If you are processing small-scale data, or processing temporary data and temporary calculations, it will be relatively suitable.
The second-floor construction of the centralized system can be used as a supplementary or transitional solution to the other two methods.
(4) Comprehensive analysis
In the value era, through the above content, we can see that it is difficult to achieve the effect of meeting needs by relying on one system alone. This is also a practical need for the second layer of Bitcoin ecological development. But how to combine these three systems requires a lot of exploration. Let’s analyze it theoretically first. Faced with different needs, there will be different combination structures.
First of all, from the perspective of the design concept of protocol layering, the Bitcoin network does not require Turing completeness. It is a global trust machine and only needs to save the data and data changes that require global trust. Based on this most basic requirement, Bitcoins instruction set can be reduced to a minimum. Other functions are left to the upper-layer extensions to complete.
Generally, small applications only need to be completed on a single blockchain. Slightly larger systems are suitable for completion on the second-layer construction of blockchain + blockchain. But for large-scale applications, the preferred solution is to use a blockchain system + distributed system.
Through the combination of multiple system structures, the limitations of the basic theory of a single system can be broken. For example, the blockchain system is limited by the limitations of the DSS impossible triangle, but if a blockchain system + distributed system is used, the impossible triangle of decentralization D, security S, and scalability S can be solved. Other combinations, blockchain + centralized system, can also solve the scalability problem to a certain extent. Distributed system + centralized system can solve the limitations of the CAP triangle in distributed systems.
3. Things related to second-story construction
With the first-tier network and second-tier construction, what is the connection between the two? Or are the two directly related? One is a direct technical connection, for example, a link through two-way locking or bridge technology. The other is correlation outside the system, such as Bitcoin and Ethereum. Although there is no direct correlation, people transform BTC into WBTC to flow on Ethereum. There is not even any technical correlation, but individual adjustments based on price fluctuations. The positions of Bitcoin and Ethereum are a correlation outside the system.
Here we only discuss technical correlations. These correlation technologies are completely closely related to the structure and characteristics of the second layer. Later, we will refer to the von Neumann structure from a more macro perspective to judge the development of blockchain-related ecology.
3.1. First- and second-layer connection technology
We have already mentioned the development of Bitcoins own technology, such as modifying OP_RETURN, SegWit (isolated witness), Taproot (isolated witness upgraded version), Schnnor signature, MAST, and Tapscript, all of which should be designed for the purpose of connecting the first and second layers. It is the basic technical element that connects the first layer and the second layer in the Bitcoin ecosystem. These connection technologies are an important part of thinking about the second-layer construction. Although there are some BTC connection technology implementation solutions on the network, such as using HashLock, or threshold signatures, MPC, etc., these solutions have limited functions and are not suitable for more complex functions. To further segment the scenarios and requirements, it is still necessary to use the basic technical elements generated for connection in the Bitcoin ecosystem.
BEVMs first- and second-layer connections are somewhat representative, and most of them use the functions built with the above basic elements. Its Shnorr signature + MAST contract + BTC L2 solution of the Bitcoin light node network is a good case for learning to connect the first layer and the second layer.
In addition to these basic technical elements connecting the first and second floors, the specific connection technologies will vary depending on the structure of the second-floor construction. Let me first briefly introduce some types of connection technologies. Common technologies for connecting the first-level network and the second-level network of the blockchain include the following:
Cross-chain technology:Through cross-chain technology, different blockchains can interoperate and realize the connection between the first-layer network and the second-layer network. Cross-chain technology can realize cross-chain transfer and interaction of assets, allowing data and value to flow between different blockchains.
Segment verification technology:Segment verification technology can isolate transaction data in the first-tier network and then verify and process it through the second-tier network. This approach can reduce the burden on the first-tier network and improve overall throughput and efficiency.
Side chain technology:Side chain technology is a technology that connects the main chain and the side chain. The side chain can realize data transmission between the first-layer network and the second-layer network. Side chains can separate some specific functions and applications from the main chain to improve overall performance and scalability.
State Channel Technology:State Channel technology is a solution based on the second-layer network. By establishing a communication channel outside the chain, transactions can be carried out outside the chain and submitted to the first-layer network only when needed. State Channel technology can increase the speed and throughput of transactions and reduce transaction fees.
Plasma Technology:Plasma technology is an expansion solution based on the second-layer network. By sharding the transaction data of the first-layer network and then verifying and processing it through the second-layer network, it can achieve higher throughput and scalability.
Common two-story structures includeBlockchain structure, distributed system structure, centralized system structure, the above common connection technologies will be different due to the different structures of the second layer, and most of them can only be used in one structure, so they will not be discussed in depth here.
As second-story construction matures, there will be more specific technologies or cases, and it may not even be a technical connection but only an economic connection.
What are the reference indicators for examining the quality of layer one and layer two link technology? The indicators you can roughly see are:
Can the first layer verify transactions on the second layer?
Can the assets on the first floor escape smoothly when the second floor collapses?
Does the connection technology degrade certain characteristics of the system?
……
The content of the link technology between the first and second layers should be better summarized and improved when there are more cases of second-layer construction. These connection technologies are currently mostly completed by second-tier builders. It is difficult to say whether there will be independent products similar to cross-chain bridges in the future.
This section is more about raising questions and allowing us participants and builders to think more.
3.2. Look at the development of blockchain with reference to the Von Neumann structure.
Previously, we have used the concept proposed by Vitalik:Blockchain is a “world computer”. Since they can all be called computers, this world computer can be compared and analyzed with the von Neumann structure of traditional computers.
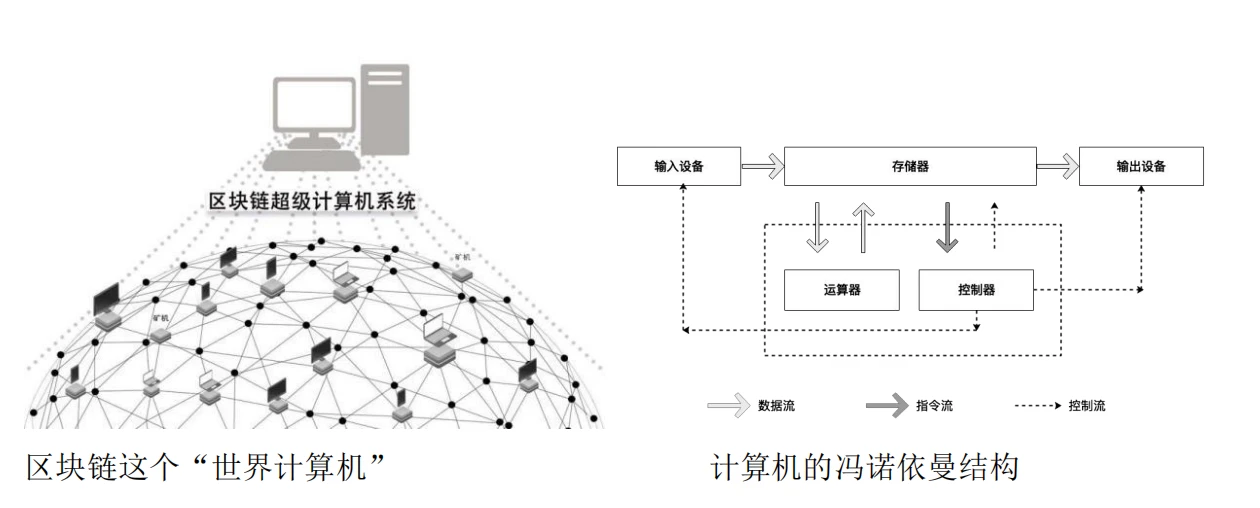
The five major components of a von Neumann architecture computer:Operators, controllers, memories, input devices, and output devices.In the world computer system of blockchain, there are similar components, and we must also pay attention to the connection part among these five components, because in a distributed system, the connection part has a greater impact.
The development rules of World Computer are very similar to the development rules of traditional computers. Compared with the development of traditional computers, the blockchain system is still at a stage similar to before 286. It is still expanding processing capabilities and storage capabilities. It has simple peripherals and is still very limited in what it can do.
Several comparisons comparing the development of traditional computers with the development of world computers:
(1) The expansion of CPU (calculator and controller) is like the expansion of current one- and two-layer computing energy and throughput;
(2) The expansion of memory will gradually shift from competing for space on the chain to using real blockchain storage. The current one- and two-layer on-chain storage spaces are like registers, first-level cache, and second-level cache in traditional computers. In the future, there will be professional blockchain storage methods such as memory, hard disk, and external storage. The current way of writing data will also change a lot in the future.
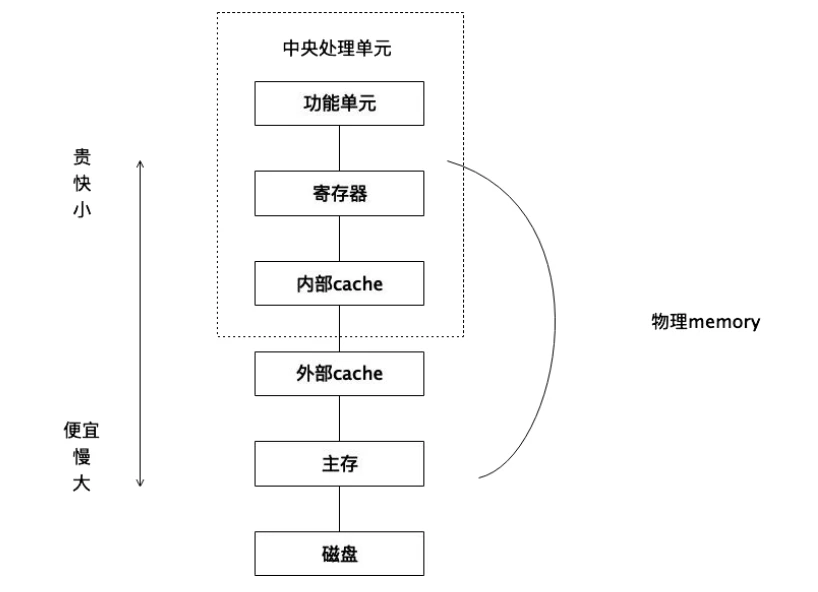
(3) Input devices and output devices, in the blockchain system, are oracles. These input and output devices have not been reflected much in the second-floor construction, and there will be more demands in upper-layer applications.
(4) Some special chains and functions in the blockchain are very similar to the GPU, special equipment cards, special peripherals and other components in traditional computers.
(5) On-chain applications and higher-level applications, just like traditional computers that have not yet distinguished operating systems and application software, are also evolving and functionally separated step by step.
(6) Many current blockchain applications are financial applications, much like early traditional computers, which are mostly used for scientific research and military applications. With development, they are slowly moving toward enterprises, families, and individuals. Blockchain applications will have a similar development trend, developing from early financial applications to broader applications.
From the construction of the second layer, there is still a lot that can be discussed comparing traditional computers and the world computer of the blockchain, which will not be described in this article.
4. Current Layer 2 construction status of Bitcoin
4.1. Bitcoin second-layer projects already in operation
In this article, we mainly introduce those second-layer Bitcoin projects that have been successfully operated, referring to some research reports and industry reports. These second-layer constructions have been running for a certain period of time, and most of them were brewed or launched from 2015 to 2019. . Some newer projects will also be introduced if they have special features. We will see that these cases are basically based on the second-layer construction of the chain, and the only distributed system construction based on the Channel is the Lightning Network. If you include the second-layer construction of Ethereum, Raiden Network is also a design case based on Channel, but its current development does not seem to be successful and will not be introduced in this article. Ethereums Plasma technology is a sub-chain design based on Channel. It seems to be a combination of chain and Channel. I personally think that its main feature is a two-layer design based on chain, so I wont discuss it too much here.
1. Lightning Network Lightning Network (based on distributed second-layer construction)
Lightning Network is a second-layer solution built on the Bitcoin blockchain and is designed to solve Bitcoins scalability and low transaction speed issues. The Lightning Network was first proposed in 2015 and fully implemented in 2018.
The main features of the Lightning Network are fast, low-cost and scalable. It establishes a series of payment channels so that Bitcoin transactions can be conducted within the channels without being directly recorded on the blockchain. This can greatly reduce transaction confirmation time and transaction fees, and support a large number of parallel transactions. The Lightning Network relies on the RMSC protocol to ensure the safety and reliability of transactions, while HTLC solves the problem of routable scalability. The scalability of its architecture gives it very high performance.
Since its launch, the Lightning Network has gained widespread attention and adoption. More and more Bitcoin users, exchanges and merchants are using the Lightning Network for fast cross-chain transactions and real-time payments. In addition, developers are constantly improving the performance and user experience of the Lightning Network, providing it with more features and scalability.
Although the Lightning Network offers significant improvements in scalability and transaction speed, it still faces several technical and adoption challenges. For example, network stability, routing algorithms and user interfaces need to be continuously improved. However, as time passes and technology improves, the Lightning Network is expected to become an important payment solution for Bitcoin and other cryptocurrencies, providing users with a faster, lower-cost transaction experience.
2.Liquid (chain-based second-layer construction)
Liquid is a sidechain solution launched by Blockstream in 2015. As the first sidechain of Bitcoin, Liquid aims to provide faster, secure and private transaction solutions to meet the needs of professional users such as financial institutions and exchanges.
One of Liquid’s key features is its fast transaction confirmation times. Compared to Bitcoin’s confirmation time of about 10 minutes, Liquid’s transaction confirmation time is only 2 minutes. This enables users to conduct transactions faster and transfer funds quickly when needed. Another important feature is Liquid’s transaction privacy. Liquid uses Confidential Transactions (confidential transactions) technology to hide the transaction amount, and only the participants in the transaction can view the specific amount. This helps protect the privacy of transaction participants.
Liquid also features higher transaction throughput. By using Federated Peg (federal anchoring) technology, Liquid can support a large number of parallel transactions and anchor on the Bitcoin network to achieve interoperability with Bitcoin. This allows Liquid to handle more transaction volume and improve overall system throughput.
Since its launch, Liquid has gradually grown in the cryptocurrency industry. More and more exchanges, financial institutions and enterprises are beginning to adopt Liquid as their trading and fund settlement solution. At the same time, Blockstream continues to introduce new features and improvements to further improve Liquids performance and security.
In summary, Liquid is a Bitcoin sidechain solution launched by Blockstream that aims to provide fast, private and high-throughput transactions. It meets the needs of professional users by reducing transaction confirmation time, providing transaction privacy, and increasing transaction throughput. Over time, Liquid has gained widespread adoption and growth in the cryptocurrency industry.
3. Rootstock (RSK) (chain-based second-layer construction)
Rootstock (RSK) is a smart contract platform built on the Bitcoin blockchain and aims to provide Ethereum-like functionality to the Bitcoin ecosystem. Rootstock was first proposed in 2015 and officially launched in 2018.
The main features of Rootstock are the two-way peg with Bitcoin and smart contract functionality. With a two-way peg to Bitcoin, Rootstock is able to use Bitcoin as its primary asset, enabling security and stability. At the same time, Rootstock supports smart contract functions, allowing developers to build and execute smart contracts with automation functions on its platform.
Since its launch, Rootstock has gradually gained recognition and adoption within the Bitcoin ecosystem. It provides more functions and flexibility to Bitcoin users and developers, allowing Bitcoin to support a wider range of application scenarios, such as decentralized finance (DeFi), digital asset issuance and supply chain management.
However, Rootstock’s development has been relatively slow compared to other smart contract platforms. Its expansion in terms of user and developer communities requires more efforts. Nonetheless, Rootstock’s development prospects are still considered positive and it has the potential to become one of the important smart contract platforms in the Bitcoin ecosystem.
4. RGB (based on distributed + Turing complete second-layer construction)
The story of RGB dates back to 2016, when Giacomo Zucco wanted to leverage Peter Todd’s concepts of client-side verification and disposable seals to develop a better Colored coins and bring these tokens to the Lightning Network (This is where the name RGB comes from). It is an open protocol built on the Bitcoin blockchain and aims to provide richer functions for the creation, transaction and management of digital assets.
RGB is a scalable and confidential Bitcoin and Lightning Network smart contract system developed by the LNP/BP Standards Association. It adopts the concepts of private and common ownership and is a Turing-complete, trustless form of distributed computing that does not require the introduction of tokens and is a non-block decentralized protocol. RGB is designed to run scalable, robust and private smart contracts on UTXO blockchains (like Bitcoin) to make all possibilities possible. Through RGB, developers can execute token issuance, NFT minting, DeFi, DAO, and more complex multi-category smart contracts.
The RGB protocol is a client-side state running on the second and third layers (off-chain) of the Bitcoin ecosystem based on the concepts of client-side validation and single-use-seals. Verification and smart contract systems.
5.Stacks (chain-based second-layer construction)
Stacks (formerly Blockstack) is a decentralized computing platform built on the Bitcoin blockchain. Stacks was first proposed in 2013 and had an initial coin offering (ICO) in 2017. Its main feature is to provide decentralized authentication, storage and smart contract functions.
The core feature of Stacks is to support the development and execution of decentralized applications with the security and stability of Bitcoin. It uses a consensus mechanism called Stacking to achieve consensus by letting users holding STX tokens lock a certain number of tokens and participate in network verification. This mechanism provides incentives for users and increases the security of the network.
In terms of development, Stacks has become one of the important platforms in the field of decentralized applications. It has attracted a group of developers and projects to join, built numerous decentralized applications, and provided a wealth of tools and development documentation. Stacks also collaborates with other blockchain projects to expand its ecosystem and application scenarios.
6. Other Bitcoin second-layer projects
With the popularity of Bitcoin, many new projects have been created. Among them, there are many projects initiated by Chinese, and these new projects such as B² Network, BEVM, Dovi, Map Protocol, Merlin, Bison, etc. also have certain characteristics.
Founded in 2022, B²Network is a second-layer Bitcoin network developed based on ZK-Rollup. It is compatible with EVM and enables EVM ecosystem developers to seamlessly deploy DApps. It is a typical case of transferring the second-layer technology of Ethereum technology to the Bitcoin ecosystem.
BEVMs original team was established in 2017 and has explored a variety of extended applications of Bitcoin. The BEVM concept proposed in 2023 is a decentralized Bitcoin L2 compatible with EVM. BEVM is based on technologies such as the Schnorr signature algorithm brought by the Taproot upgrade, allowing BTC to cross-chain from the Bitcoin main network to Layer 2 in a decentralized manner. Since BEVM is compatible with EVM, all DApps running in the Ethereum ecosystem can run on BTC Layer 2 and use BTC as Gas. On November 29, 2023, BEVM released a white paper.
Founded in 2023, Dovi is a Bitcoin Layer 2 compatible with EVM smart contracts. In November 2023, Dovi officially released the white paper. According to the white paper, Dovi integrates Schnorr signatures and MAST structures to improve transaction privacy, optimize data size and verification processes; issue a flexible framework for various asset types other than Bitcoin, and realize cross-chain asset transfers.
The Map Protocol team was established relatively early. It originally focused on cross-chain protocols, which are the first- and second-layer connection technologies we introduced earlier. After the Bitcoin ecosystem became popular, it will soon be able to build a second-layer construction based on the chain. The ability to cross-chain current inscription assets and reduce transaction costs will attract some project parties and applications.
From the official website of Merlin Chain, it is easy to see its Bridge attributes. It transfers assets on BTC to the second-layer network and reduces transaction costs. It is a typical representative of solving pain points first. According to the official website introduction and some research reports, Merlin is a Bitcoin Layer 2 solution that integrates the ZK-Rollup network, decentralized oracles and on-chain BTC fraud prevention modules. The project is launched by Bitmap Tech. They are a unique team. The Bitmap.game and BRC-420 Blue Box Ordinals assets they launched have good reputations.
Founded in 2023, Bison is a Bitcoin-native zk-rollup that increases transaction speed while enabling advanced features on native Bitcoin. Developers can use zk-rollup to build innovative DeFi solutions, such as trading platforms, lending services, and automated market makers. From its official website, Bridge is also an important feature. Cross-chaining Bitcoin assets and completing upper-layer asset applications is the entry point for many projects.
Judging from the above relatively new projects B² Network, BEVM, Dovi, Map Protocol, Merlin, and Bison, they have quickly completed the reduction of transaction fees and met the transaction needs of Bitcoins first-level assets. They all involve cross-chain assets. Those teams that have cross-chain protocols can do it faster. Teams that have experience in second-layer construction have more advantages in upper-layer applications. These newer projects are all based on the second-layer construction of the chain, taking advantage of the original technology accumulation and short-term explosive power. These projects are somewhat homogeneous. What will be their future development? What will be the outcome of competition with distributed second-tier construction service providers? It also requires a lot of observation. Judging from the experience of second-tier projects on Ethereum, many projects will fall flat after the tokens are issued through hot-spot marketing. Will this be the case for Bitcoins second-tier projects?
From the projects currently running on the second layer of Bitcoin, we can roughly see that the well-known second-layer Bitcoin projects were established relatively early and have been exploring related technologies for a long time. However, because the basic technology of the Bitcoin ecosystem has not been formed, the project Most of them are not exciting enough, or they are overshadowed by the light of Ethereum and the Ethereum ecosystem. With the maturity of Bitcoins basic protocols, especially the formation of underlying technologies such as Segregated Witness, Taproot, Schnorr signatures, MAST Merkle abstract syntax tree, and Tapscript, the connection technology between the first layer and the second layer has developed better. As a result, the things that the Bitcoin ecosystem can do are becoming richer. From the second-layer projects of Bitcoin that are already running, we can see that some are builders of the original Bitcoin ecosystem, another part are builders of the second layer of Ethereum, and some are builders from connection technology. No matter which direction the project comes from, it needs to use these newly generated Bitcoin basic connection technologies. The more fully and diversified the methods of use are, the better the support for the second layer will be.
4.2. Development analysis of Bitcoin’s second-layer construction
Wherever the funds are, there will be enthusiasm, and it will attract more funds to gather. Bitcoin currently has a market value of approximately US$800 billion. Its ecological development is weak, but it has the potential to explode. Therefore, many projects claim to carry out the second-layer construction of Bitcoin. We will not mention the specific names of these projects here, but we will make some classifications of the entrants of these projects to see their characteristics and their respective advantages and disadvantages.
1. Original Bitcoin second-layer construction project
The original second-layer Bitcoin projects, especially those that have been developed for many years and have certain accumulated advantages, can they be rejuvenated by the popularity of Bitcoin this time? Will it thrive? There is great uncertainty.
There are two measurement criteria: First, as mentioned earlier, whichever second-layer network has a higher total locked-up value TVL will win out. The other is the two-layer structure type. The chain-based two-layer construction will accommodate more parallel players because of its expansion characteristics. The distributed two-layer construction can only accommodate relatively few competitors.
The original second-tier projects still need to give full play to their accumulated advantages and establish new advantages with the help of new technologies to attract more applications to the platform. Only then can they have the opportunity to rejuvenate and gain more market share. If it fails to attract more applications, such old projects are likely to eventually sink or transform. In fact, such projects can also cooperate or merge with projects that have no technical accumulation at all and have established a community through some consensus through some consensus in exchange for greater development.
In addition, if those old projects can have advantages in the accumulation of distributed-based second-tier construction technology, they can fully intervene in the distributed-based second-tier construction, and it will be more effective by providing guidance for upper-layer applications.
2. Newly entered Bitcoin second-layer construction projects
New projects that enter the second-layer construction of Bitcoin generally do not have many accumulated advantages, but this gives such a team the advantage of being a latecomer. They can research the latest technology, solve the lightweight and most attractive needs first, and attract a certain number of people. Application entry. It is best to have a team with second-layer construction experience in the Ethereum ecosystem or other ecosystems, which is more suitable for quickly entering the second-layer construction of Bitcoin. For such a project, you can consider chain-based second-layer construction, which will be faster and more advantageous.
Teams with absolutely no experience or advantages can refer to the third scenario to see if they can screen out users and accumulate funds through community consensus.
3. Bitcoin second-tier projects that have no accumulation but want to enter
I didnt have much understanding of projects that promoted Web3.0 without any technical or community accumulation. I most likely considered these projects to be CX projects. But through the phenomenon of inscriptions, those communities that have generated a large community consensus through a certain inscription, such as sats, ordi, and rats, not only have many members, but also accumulated a certain amount of funds. Such a project can completely start a new second-layer construction from scratch. Through the power of the community, upper-layer applications can be integrated into the community. At the same time, it is possible to build a second-layer. Such a second-layer will most likely be chosen to be chain-based. The second-layer construction is simple and fast, and through the power of the community, DID (decentralized identity), DAO tools, DeFi applications, and other upper-layer applications are built on the second layer of the community, and there is no need to build it yourself, only need to introduce it Mature product parties and share revenue sharing with them. This may form a small ecology. Such projects place higher demands on community construction, foundation management, and decision-making mechanisms.
4. Development of upper-layer applications
With the rapid development of Bitcoins second layer, the huge amount of funds sleeping on BTC began to be reawakened, and due to the eyeball effect, more new users will be attracted to enter the Web3.0 field, coupled with the rapid development of Bitcoins second layer technology , will lay a solid foundation for Mass Adoption. The upper-layer applications will start from the current financial applications and gradually introduce applications that require high performance, large traffic, and frequent interaction, such as Gamefi, SocialFi and other applications. There will be no downtime of chain-based applications and poor service experience. Good situation. The development of Bitcoins second layer will bring many opportunities and solid infrastructure to upper-layer applications. When mature, it will bring more opportunities to more less-Native Web3 teams.
In any case, the Web3.0 era has just begun. It is still in its infancy and early stages and requires a lot of exploration and construction. Many countries and regions are not yet fully open to many new things in Web3.0. Web3.0 requires a lot of construction and will give each project team more opportunities. A team that constantly senses new developments and new technologies, constantly adjusts, and constantly participates in the construction of Web3.0 will definitely gain something at a certain stage and in a certain field.
Reference description
Writing this article is the result of my reading a large number of industry articles and participating in many activities such as TwitterSpace and offline communication. Inspired by what many people said, some of the prominent influencing people and factors are as follows:
(1) Teacher Dashan from Waterdrop Capital. He has written many articles, given many lectures to us on the Island of All Things, and participated in many Space activities in which he participated.
(2) Some in-depth technical content is obtained by listening to Teacher Hong Shuning’s lectures, watching his videos, and communicating with Teacher Hong Shuning offline, such as routing problems in distributed systems and RGB Turing completeness problems.
(3) Numerous articles on www.btcstudy.org. There is a wealth of knowledge compiled on this website.
(4) Interview program with Jan Xie, chief architect of Nervos (CKB).
(5) Read more about BIP protocol, Segwit, Taproot, ordinals, brc 20, Atomical, etc.
(6) Other blockchain knowledge, including hierarchical design ideas and the comparison of von Neumann structures, are derived from the accumulation of knowledge I wrote in several books in the past few years, of which 5 were published, Blockchain Knowledge-Popular Popular Edition, Blockchain Knowledge-Technology Popular Edition, Turing Blockchain, Blockchain Economic Model, Web3.0: Building the Digital Future of the Metaverse; and 3 books on Ethereum, completed Part of the writing was done but has not been published. These contents refer to a lot of native protocols, white papers, and technical principles of the blockchain. The output of these contents is also the result of everyone. I just collected and organized them. Slowly, I understood the correlation between these underlying principles and many technologies and possible future application scenarios.
(7) Discussion and thinking with team members when designing related products in our project.
I am very grateful to Mr. Dashan of SatoshiLab, Elaine Yang, Hong Shuning and related technical experts. They read this article and gave a lot of feedback and revision opinions. They strictly control the accuracy of the concepts cited in the article and will not confirm it until we can find the original reference. , I really appreciate this rigorous habit! Many thanks to all contributors and participants who have improved my body of knowledge.










