Original | Odaily Planet Daily ( @OdailyChina )
Author: Azuma ( @azuma_eth )

The popular project Hyperliquid (HYPE) today suffered the largest round of pullback since its launch.
Bitget market data shows that as of around 14:00 Beijing time, HYPE was temporarily reported at 26.21 USDT, with a daily drop of up to 20.5%.
Are North Korean hackers targeting Hyperliquiquid?
Looking at market news, the most discussed event in the Hyperliquid community today was a warning from the well-known security researcher Tay ( @tayvano_ ) - multiple marked North Korean hacker addresses have been trading on Hyperliquid recently, with a total loss of more than US$700,000.
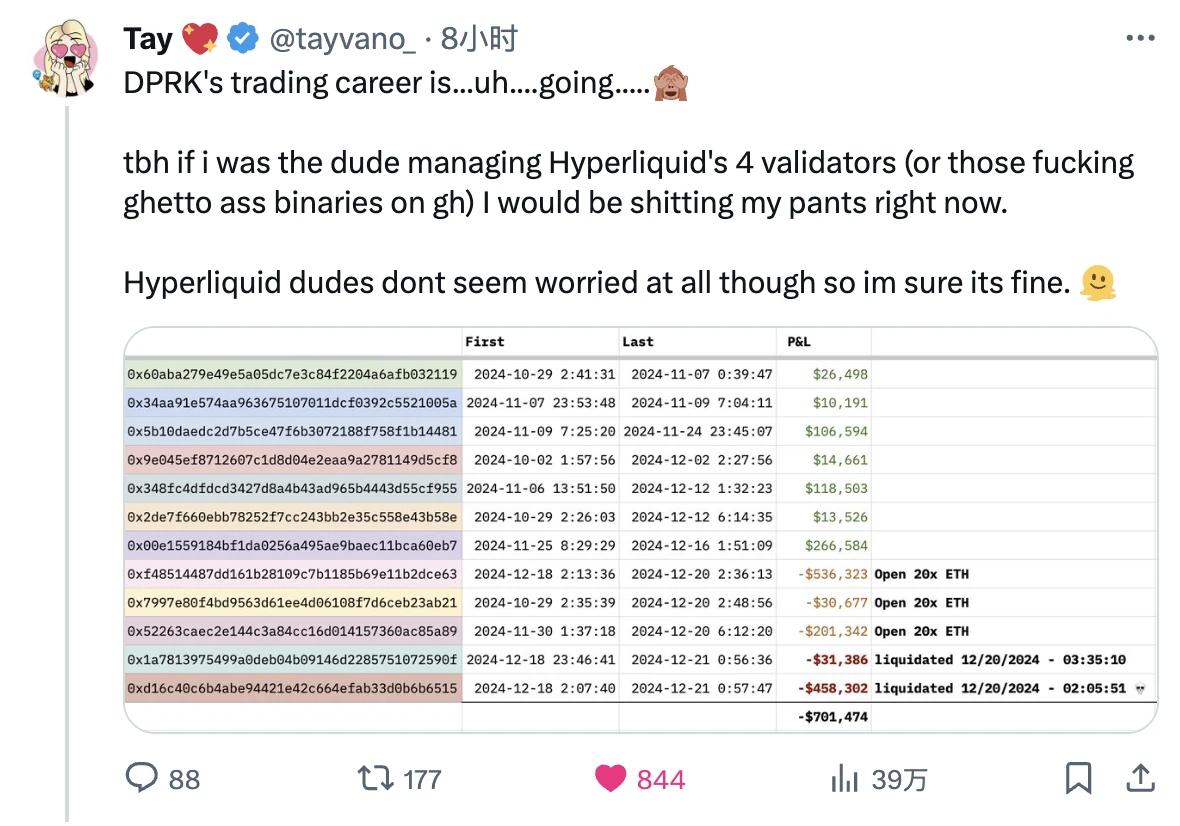
Although Hyperliquid has not shown any signs of being attacked as of the time of writing, as Tay said, If I were one of the four validators managing Hyperliquid, I would probably have pissed my pants right now ... Signs of activity from the most powerful hacker force in the cryptocurrency world may mean that North Korean hackers have identified Hyperliquid as a potential target and are testing the stability of the system by executing transactions.
After Tay’s post was published, it immediately sparked heated discussions within the community, especially the issue of “4 validators” mentioned by Tay, which sparked heated discussions. Some community users even regarded it as the weakest link in the current Hyperliquid system security.
Potential threat: $2.3 billion relies on 3/4 multi-signatures only
Abstract developer cygaar explained that there are currently $2.3 billion worth of USDC in the Hyperliquid bridge contract deployed on Arbitrum, and most of the functions in the bridge contract require 2/3 of the validators’ signatures to execute (because there are only 4 validators, so actually 3 signatures are required).
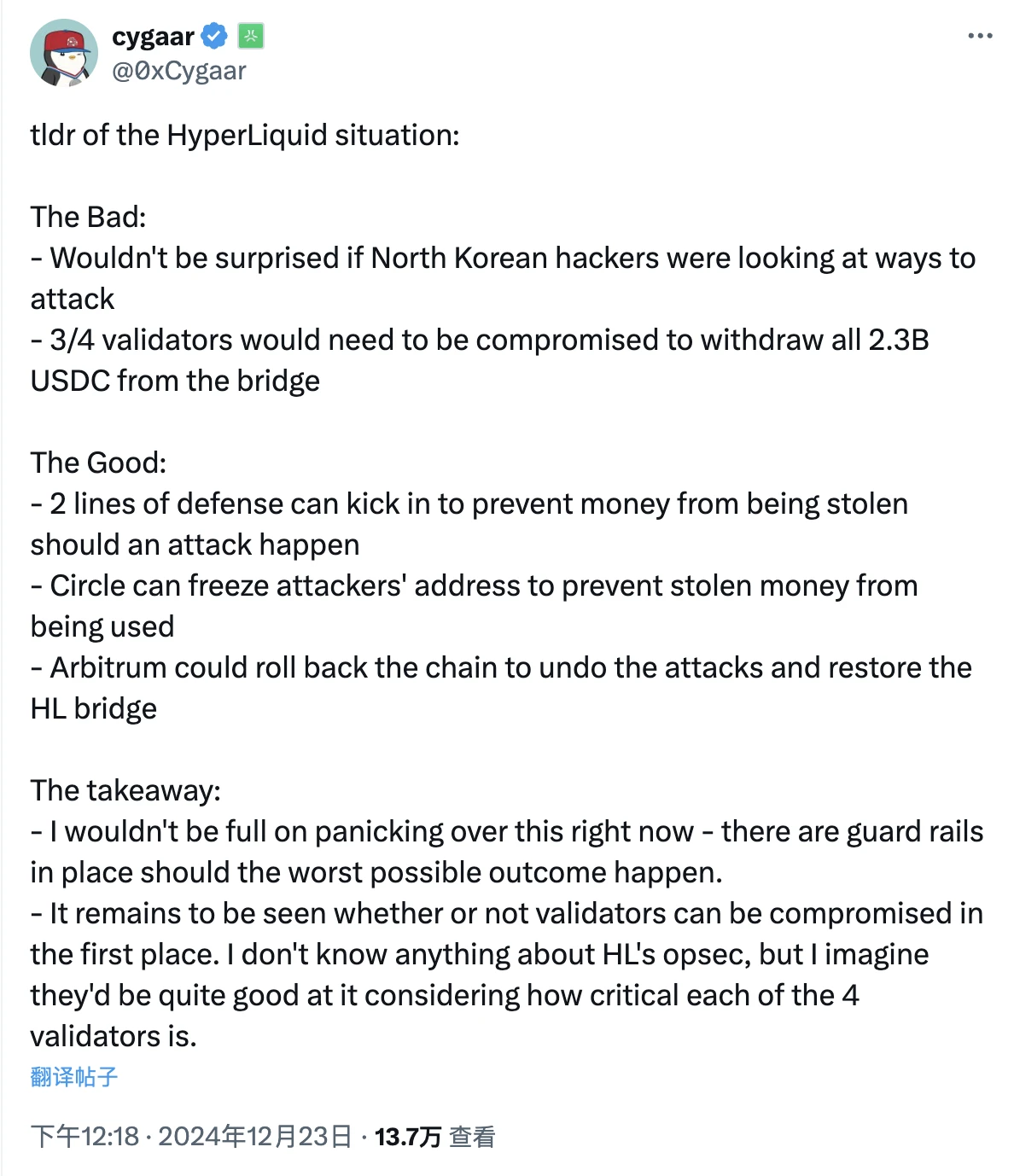
Assuming that the majority (3/4) of validators are compromised, the compromised validator can submit a request to withdraw all USDC on the bridge contract and send them to a malicious address. Since the attacker has controlled the vast majority of validators, they will be able to pass and finalize the withdrawal request smoothly, which means that $2.3 billion of USDC will be transferred to the attacker.
There are currently two lines of defense that can intervene to prevent these USDC from being lost forever.
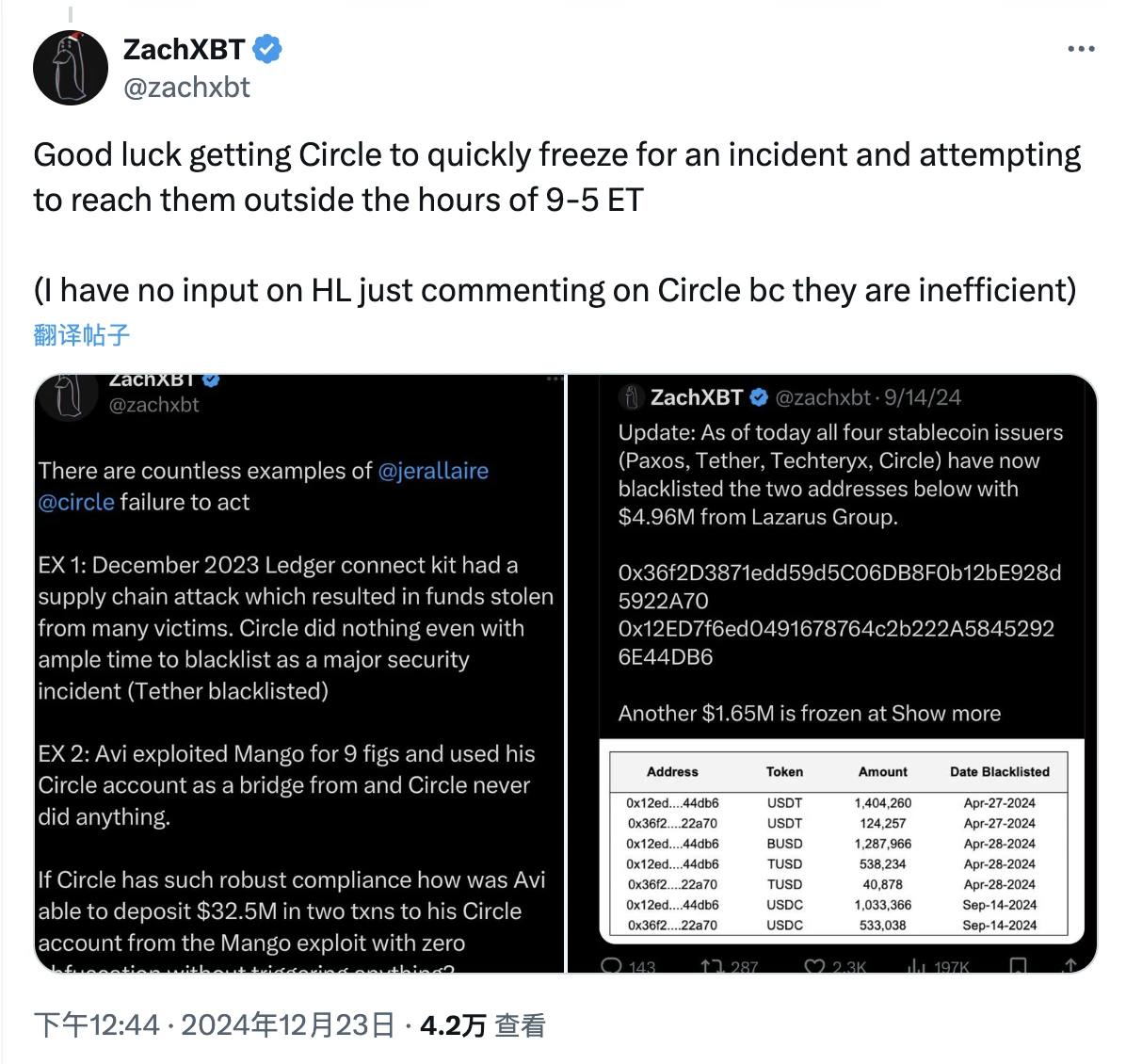
The first line of defense is at the USDC contract level. Circle’s blacklisting mechanism can completely prohibit specific addresses from transferring USDC. If they act quickly enough, they can prevent the attacker from transferring the stolen USDC, effectively freezing the funds and repaying the Hyperliquid bridge contract .
In response to this line of defense, security guru ZachXBT commented that Circle is very inefficient and dont expect them to make any remedies, but ZachXBT also clarified that the comment was only directed at Circle and did not involve his opinion on Hyperliquid.
 The second line of defense is at the Arbitrum network level. Currently, the Arbitrum L1/L2 bridge contract on Ethereum is protected by a 9/12 multi-signature contract (the Security Committee). Suppose the attacker somehow took control of the 2.3 billion USDC and immediately exchanged it for other tokens, thereby circumventing Circles blacklist mechanism. In theory, Arbitrums Security Committee could also change the state of the chain, rolling back and preventing the original attack transaction from occurring. In an emergency situation, the committee could vote on whether to make such an intervention.
The second line of defense is at the Arbitrum network level. Currently, the Arbitrum L1/L2 bridge contract on Ethereum is protected by a 9/12 multi-signature contract (the Security Committee). Suppose the attacker somehow took control of the 2.3 billion USDC and immediately exchanged it for other tokens, thereby circumventing Circles blacklist mechanism. In theory, Arbitrums Security Committee could also change the state of the chain, rolling back and preventing the original attack transaction from occurring. In an emergency situation, the committee could vote on whether to make such an intervention.
Cygaar added that this last line of defence is obviously highly controversial and should only be used in the most dire situations.
Deliberate FUD or well-intentioned warning? Community reactions are mixed
The communitys reaction to Tays warning post was sharply polarized.
On the one hand, some community members believe that Tay’s warning was exaggerated, especially after the decline of HYPE, and many community users believe that Tay is just deliberately FUDing.
Some community members pointed out that North Korean hackers will target every protocol with a high TVL, not just Hyperliquid. Simply finding traces of hackers use does not mean that the protocol has been threatened.
Some community members also pointed out that Tay actually works for Consensys, and his so-called warning was suspected to be motivated by interests. In fact, it was just for Consensys to achieve the most favorable cooperation with the Hyperliquid team.
On the other hand, some celebrities have chosen to support Tay’s safety efforts.
Well-known white hat hacker samczsun said that although Tay has served the cryptocurrency industry for free for several years, he was heavily criticized for this post simply because the price of HYPE fell sharply after the warning was issued... It is really sad to see such news.
Evgeny Gaevoy, founder and CEO of Wintermute, also said that Tays communication style may be a bit rough (after the tweet was posted, Tay and some users who accused him had a fierce exchange of words), but you cant ignore messages like this.

In short, for Hyperliquid, which has been going smoothly since its launch, todays discussion can be said to be a minor accident in the operation of the project. It is not a minor accident because Hyperliquid was not actually attacked; it is not a minor accident because some vulnerable links at the Hyperliquid system level were exposed, and the community consensus was diverted to a certain extent on this incident... However, as a leader who is determined to change the rules of the industry, this accident is more of a touchstone than a difficulty. How Hyperliquid will solve the 3/4 multi-signature problem and calm UFD in the future will also be a good opportunity for the market to re-evaluate the quality and efficiency of the project.










