Original | Odaily Planet Daily
Author | Nanzhi

Yesterday, X user @CryptoNakamao posted a message saying that due to the malicious Chrome plug-in Aggr, his browser cookies were hijacked. Hackers manipulated his Binance account in this way and caused losses of 1 million US dollars through cross-trading.
In response to the incident, Binance issued a statement saying that the incident occurred because the users computer was hacked, and the security customer service took 1 minute and 19 seconds to handle the users freezing request. The platform checked the knock-on transaction, confirmed the suspects account, and required time to make a freezing request across platforms. As of the current investigation results, Binance did not notice the relevant information about the AGGR plug-in before this incident. Therefore, no compensation can be made for such incidents.
This incident once again sounded the alarm for security for the majority of users. As hackers become more professional, security incidents are often beyond the reach of even the gods. Therefore, although how to do a good job of security prevention is a commonplace topic, it deserves the highest priority. Odaily will summarize common attacks and prevention methods in this article.
Freeze account with one click
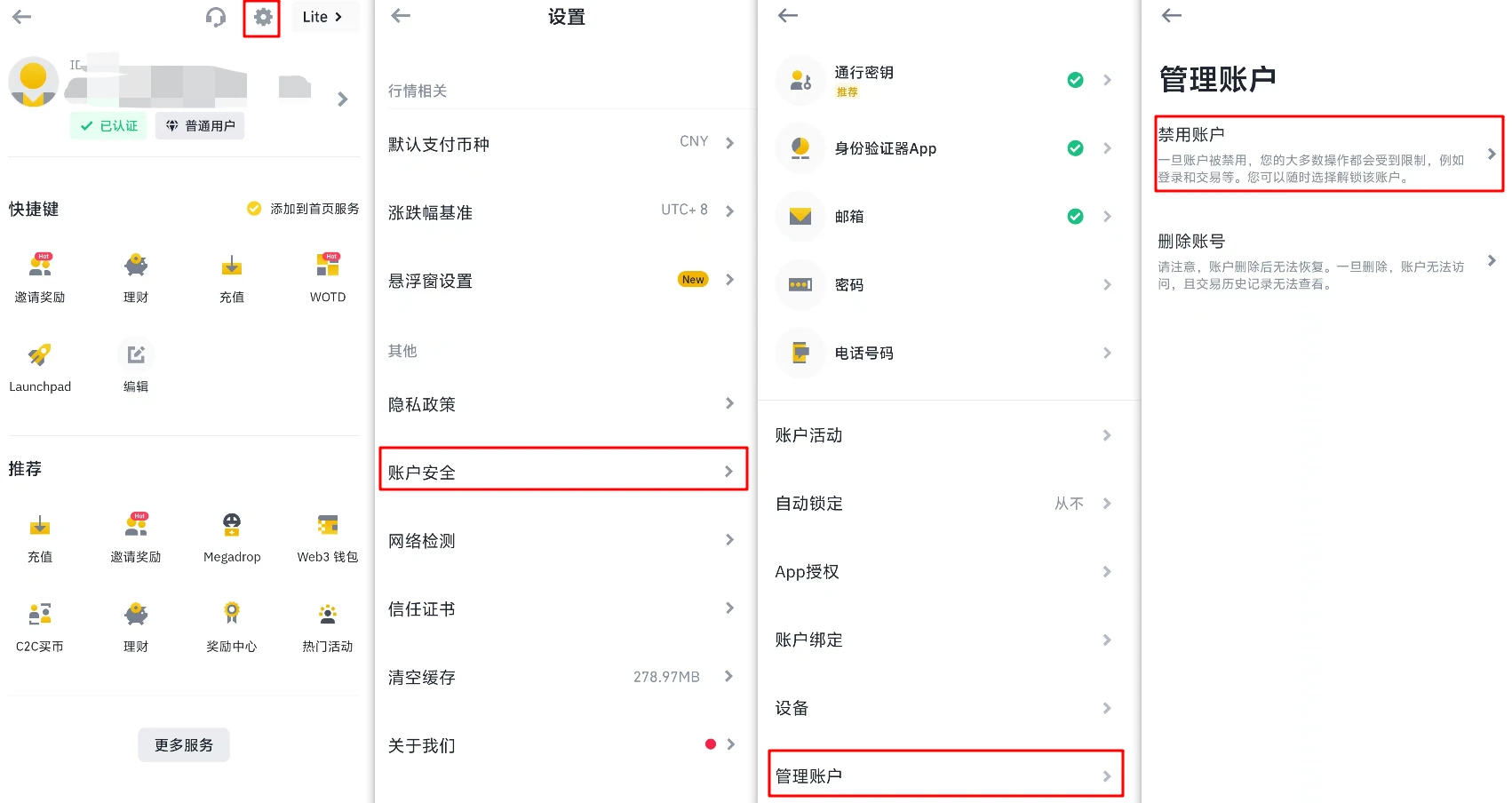
First of all, regarding this incident, if you find that you have been hacked, but the funds in your account have not been completely transferred, how can you protect the remaining funds as quickly as possible? In addition to transferring funds to other accounts, you can also protect your account by disabling it with one click. After disabling, you need to contact customer service to unfreeze it.
To disable an account, you need to go to the Binance App. First, go to the settings interface, then there will be an Account Security section at the bottom of the interface, and finally go to Manage Account at the bottom of the section, click on the disabled account and confirm. Binances current official guidance is the 2018 version, and the specific execution process is very different from the reporters current practice. It is recommended that users confirm and familiarize themselves with the specific location in advance.
Chrome extension
Chrome plug-ins are indispensable for Crypto users, so it is not realistic not to use plug-ins. So how to use Chrome safely? Users can do the following:
Check browser plug-in permissions and disable infrequently used browser plug-ins;
Open multiple browsers and assign different browsers to businesses with different security requirements;
All Chrome plug-ins are recommended to be redirected through the links provided by the official X account. It is not recommended to use Google search, let alone X-degree search. Searching through the above channels is likely to encounter paid phishing links, which will cause losses. The official has the obligation to keep the X account link correct, and even needs to compensate users in the event of an attack.
Installed plugin permissions view
SlowMist has written an article to explain the principles and security issues of Chrome extensions. SlowMist Chief Security Officer 23pds pointed out that the most critical thing is the manifest.json file, which determines the scope of the plug-ins permissions.
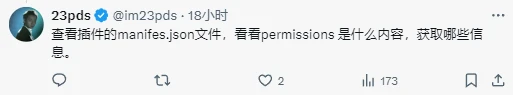
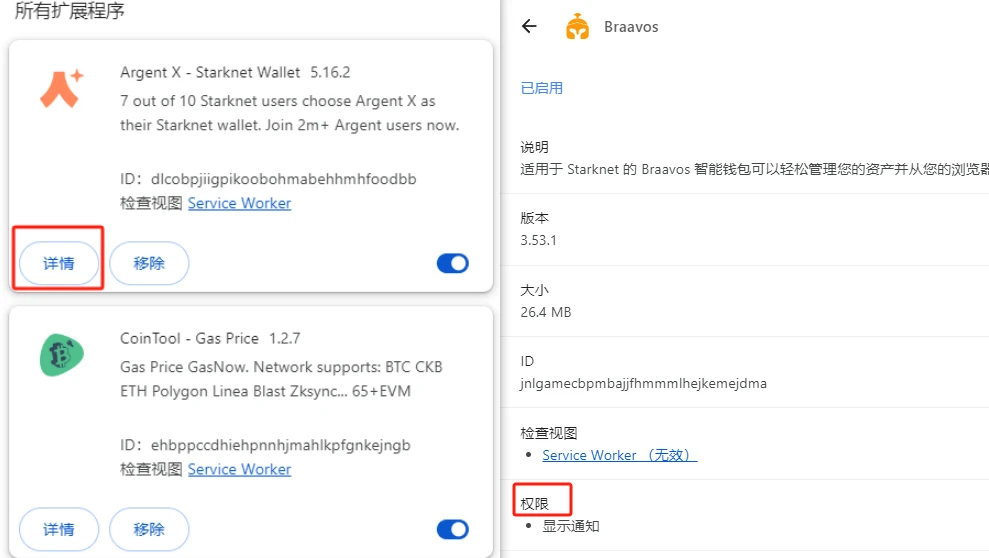
How to check the scope of permissions? Users can go to the chrome://extensions interface, which includes all the plug-ins installed on the browser. After clicking on the details, you can see the scope of the plug-in permissions. For plug-ins with permissions of Read and change all your data on all websites, you need to be very careful.
Multiple browsers
Users can implement security protection by assigning different browsers to businesses with different security requirements. For example, no plug-ins are allowed on the browser used to log in to the exchange, and only basic tools such as secure wallets are used on browsers involving on-chain funds.
There are two common ways to open multiple Chrome browsers:
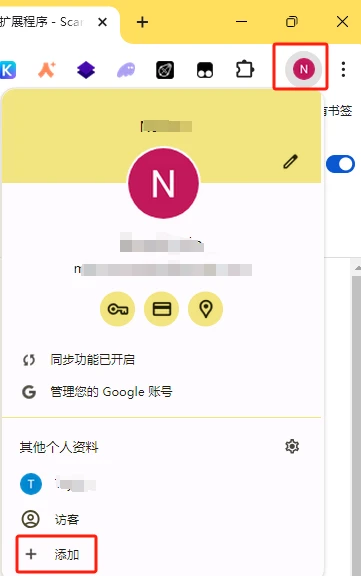
The first method is to open multiple accounts through the official account switching method. In the account interface in the upper right corner of Chrome, users can choose to add a temporary guest account or a Google account. After adding, click Add Account to open a new browser interface. Browsers opened by different accounts run independently, and plug-ins cannot do evil across browsers. And compared with the next method, it has the advantage of plug-ins being synchronized in the cloud.
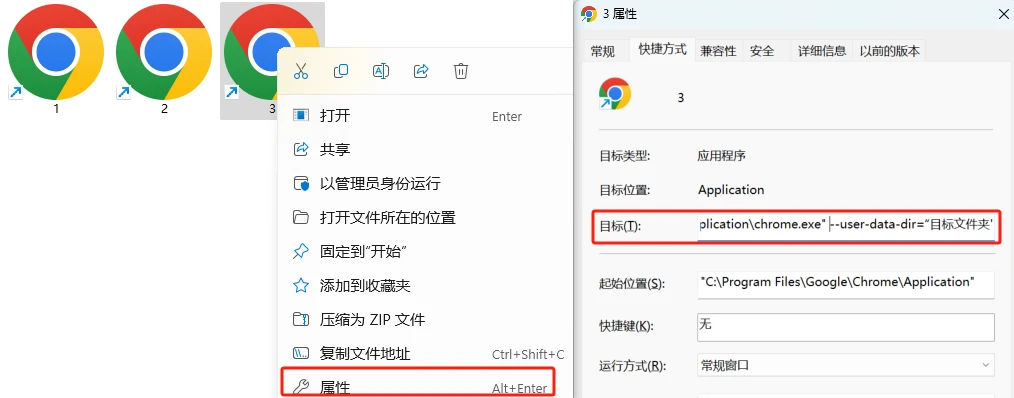
Another common batch creation method is to open multiple files based on computer shortcuts.
Users can copy one or any number of Chrome shortcuts on the computer, then right-click on the shortcut to enter the properties interface, and enter
--user-data-dir=target folder address
You can create a new independent Chrome browser (note there is a space at the beginning). This method is faster than the previous one, but you need to pay attention that the data is saved locally, and you need to back up key data such as wallet keys.
Clipboard permissions
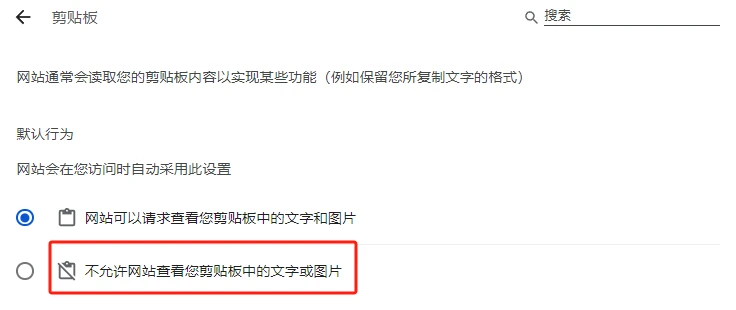
Due to the prevalence of TG Bot, many users tend to copy the secret key directly. In this scenario, it is recommended not to copy the entire secret key at once. You can save a few letters for manual input to avoid the risk of clipboard monitoring. In addition, it is also very important to turn off the clipboard reading permission of APP and web pages. For web users, you can go to the following link chrome://settings/content/clipboard, where you can turn off the websites reading permission and turn it on again when necessary, which can greatly improve security.
X platform fake account scam
In recent months, there have been frequent cases of counterfeiting official accounts to post malicious phishing links on platform X. These accounts are often gold-label accounts, with the username consistent with the official one, and only one or two letters different in the account handle, which is difficult to tell at a glance.
For this type of scam, users are advised to install the Scam Sniffer plug-in , which will scan X platform accounts and alert fake official accounts that appear in the comment section.
Other basic safety awareness
In addition to the above manual inspection and switch safety operations, there are many basic awareness-level safety factors, including:
Do not trust any private message links on TG and DC, only trust official accounts that post links and information;
Try not to use the internet for your mnemonics and secret keys, especially don’t use your phone to take photos to record your mnemonics;
Avoid installing remote control software such as Todesk and Sunflower on computers involving large amounts of money;
For exchange accounts involving large amounts of funds, set up 2FA and log out of the account after use;
Decentralization means that security issues will never disappear and losses will be difficult to recover. Hackers’ attack methods are still constantly upgrading. Only you can protect yourself. Doing the most basic security protection is the key to survival.










