Introduction Recently, Bitcoin L2 project Bitlayer Labs completed a $11 million Series A financing, led by Franklin Templeton, ABCDE and Framework Ventures. At the same time , Bitlayer became the first Bitcoin infrastructure project to receive institutional investment from an ETF license.
Bitlayer is a BTC L2 project, with the original intention of improving the scalability of BTC and unlocking the potential of its ecosystem . In terms of project features, Bitlayer is the first L2 based on BitVM , and also the first L2 that fully inherits BTC security and is Turing complete.
1. Current status of BTC L2
The essence of BTC L2 is a cross-chain bridge. Currently, the cross-chain bridge solutions of L2 projects have their own characteristics, but from a technical point of view, the essence of most cross-chain bridge solutions is multi-signature.
The multi-signature scheme actually has serious trust issues, and fund thefts due to multi-signature are common.
The author believes that as a supplement to L1, L2 should not be limited to the expansion of the ecosystem, but should also inherit the security of L1.
As the first L2 based on BitVM, Bitlayer has achieved trust minimization and a good balance between security and scalability. Next, let’s follow the technical perspective of Shisijun to explore how Bitlayer can expand BTC as an L2 while taking security into consideration.
2. Bitlayer-L2 that takes into account both security and scalability
2.1 Basic Architecture of Bitlayer
The basic architecture of Bitlayer is shown in the figure below (refer to the Bitlayer white paper, see the appendix) .
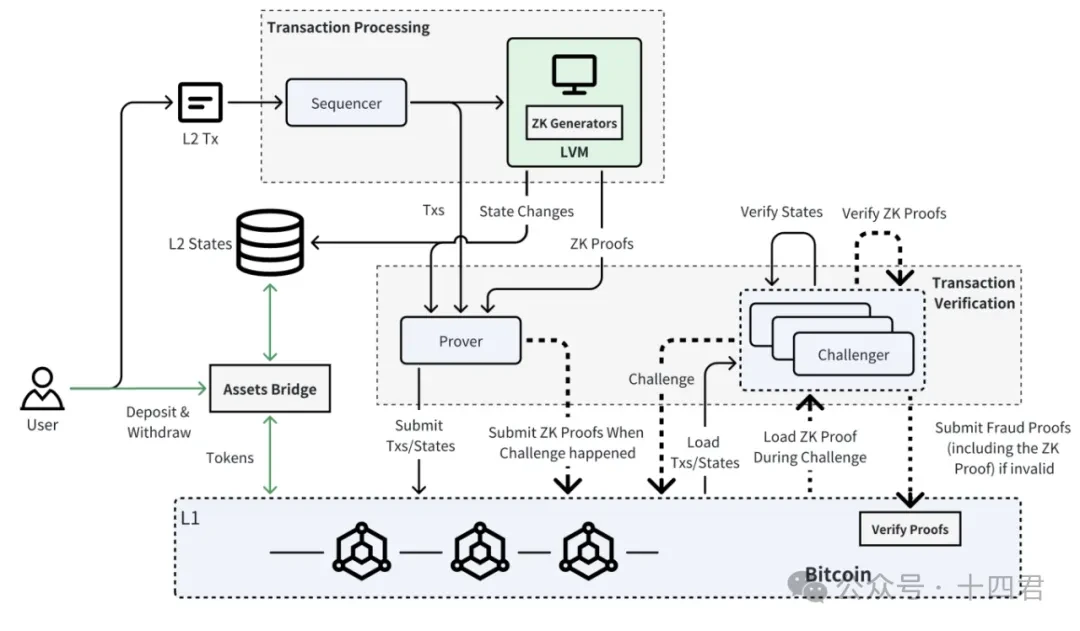
It can be seen that Bitlayers business process can be divided into three stages: transaction processing, transaction verification, and final verification. The components that interact in each stage and their general processing flow are shown in the following table:
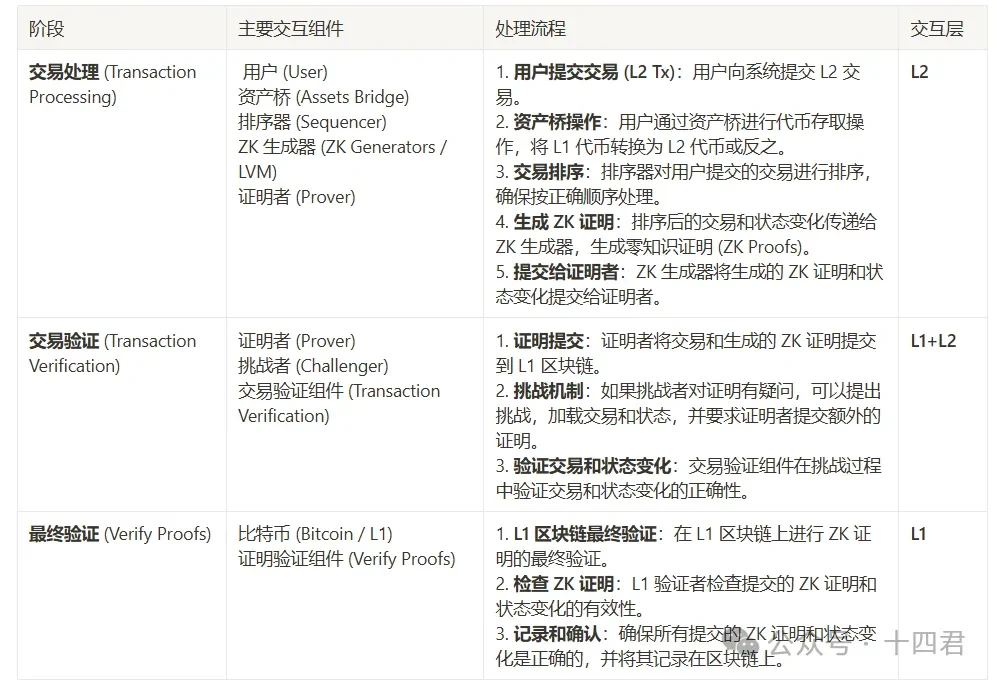
Lets disassemble the core process of Bitlayer.
2.2 Transaction Processing Phase - Layered Virtual Machine LVM
In the transaction processing stage of L2, there are two components: the sequencer and the LVM (layered virtual machine).
Without going into too much detail about the sequencer, the sequencer in Bitlayer is responsible for collecting cached transactions and sorting them, and is the entry point for transactions in Bitlayer.
LVM is the computing component of Bitlayer, and its functional responsibilities are to execute smart contracts and generate the latest status and zero-knowledge proofs.
What are Tiered Virtual Machines?
To answer this question, let’s look at the following picture (refer to the Bitlayer white paper, see the appendix) .
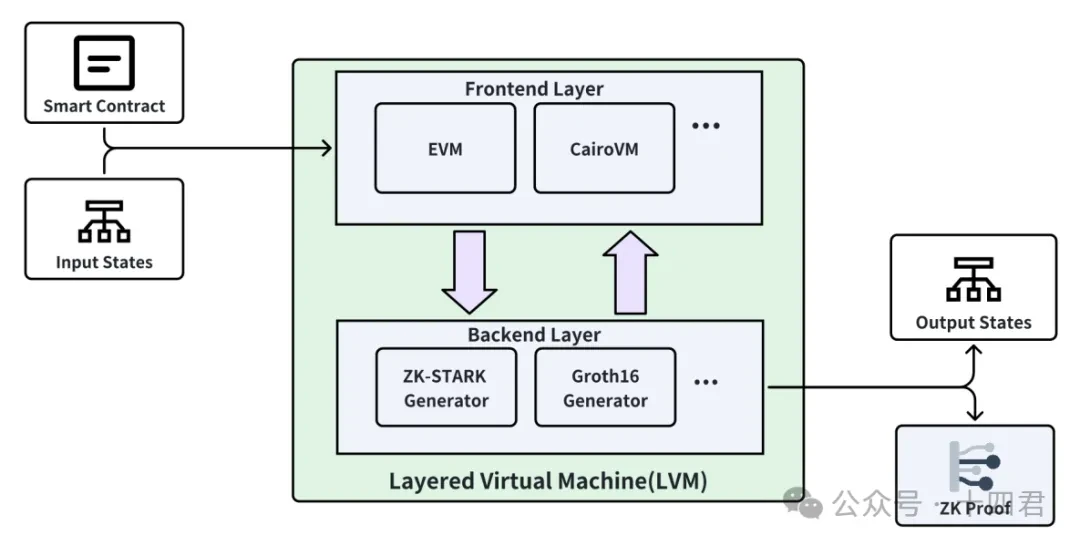
Unlike conventional VMs, Bitlayers LVM decouples the execution of front-end smart contracts from the back-end zero-knowledge prover. VM and zero-knowledge prover exist as components in LVM. This innovation allows Bitlayer to expand support for various contract types and various zero-knowledge proof verifiers, greatly improving the scalability and security of the system.
2.3 Transaction Verification Phase-OP Bridge Based on ZKP
The verification phase of the transaction is actually the interaction phase between L1 and L2. When assets flow between L1 and L2 in the form of transactions, we are faced with the classic L2 cross-chain problem: How can L2 inherit the security of L1?
Classic L2 cross-chain problem: How does L2 inherit the security of L1?
In fact, there are already very mature solutions on ETH. The current mainstream and secure ones are mainly ZK Bridge and OP Bridge. Please refer to the following table for a comparison between the two:
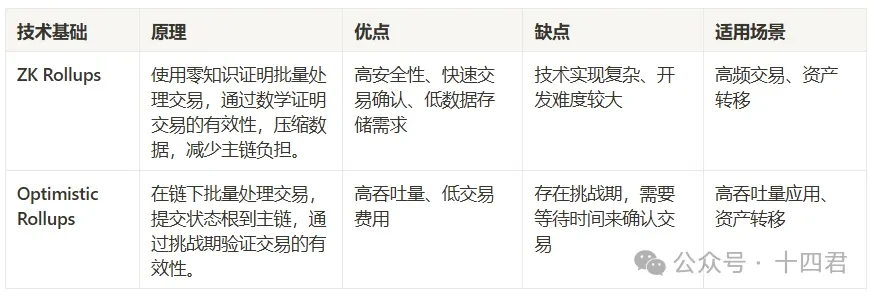
The ZK bridge itself is the most secure cross-chain bridge solution currently because it does not require trust. The OP bridge uses fraud proof to challenge invalid cross-chain data on the chain (1-N security model) to ensure the security of cross-chain data. It seems that the ZK bridge is safer than the OP bridge, but in fact, the BitVM that the Bitlayer core relies on chooses the OP bridge.
Why OP Bridge?
The main reason is still technical limitations. Currently, only the ZK bridge for BTC L1→L2 deposit direction can be realized. For L2→BTC L1 withdrawal, only multi-signature bridge or OP bridge is currently supported. Bitlayer chose the safer OP bridge for security reasons, which is actually a compromise.
The Bitlayer cross-chain bridge solution is a combination of the BitVM bridge + the OP-DLC bridge. The OP-DLC bridge is a supplement to the BitVM bridge.
BitVM OP-DLC Dual Combination Bridge Process Analysis
Bitlayer uses the Bitvm bridge to ensure security, while supplementing OP-DLC to reduce dependence on BitVM. So far, the BitVM bridge has undergone several upgrades, achieving a leap from pure theory to practice.
The latest flow chart of BitVM Bridge is as follows:
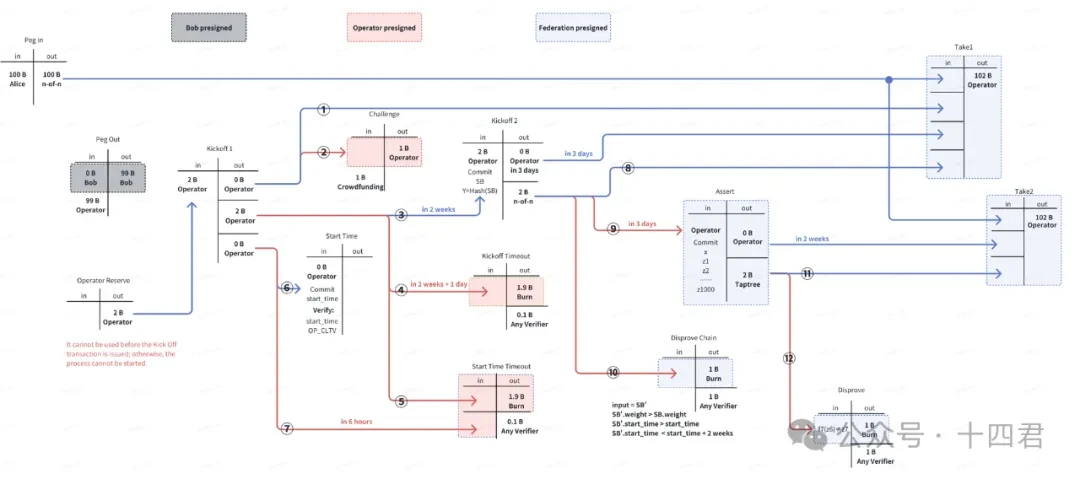
There are a total of 5 roles in the whole process.
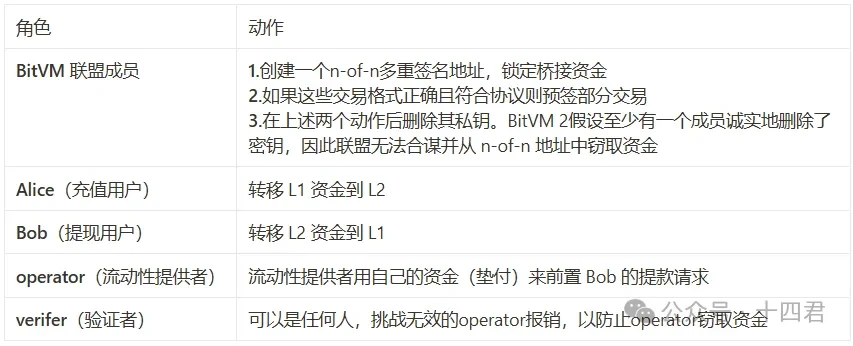
How to understand this pattern?
From the perspective of the model, the BitVM bridge is based on the model of advance payment and reimbursement. The Operator node advances funds for the withdrawal users, applies for reimbursement from the public deposit address regularly, and earns fees by taking advantage of the price difference (the handling fee from the withdrawal users). If the Operator misrepresents transaction data, it can be challenged and punished by anyone.
So is security guaranteed?
We all know that cross-chain fund transfers rely on a public fund pool (essentially assets locked by users). The security of the fund pool is a core issue that all cross-chain bridges must solve.
Traditional BTC L2 solutions generally manage public fund pools through multi-signatures, which obviously has trust risks. The BitVM bridge adopts a similar idea to the Lightning Network, which pre-specifies who can take the funds . When users lock funds into a public fund pool, they will communicate with the alliance so that the funds are locked in a Taproot address and can only be collected by the Operator. The Operator can only unlock the relevant funds after the advance payment is completed, the proof of the advance payment is provided to the chain, and it is challenged correctly.
It can be said that the BitVM bridge has achieved the splitting of the fund pool by introducing the Operator, which is indeed a novel idea. Based on past experience, we will habitually think about how to achieve decentralized fund management methods, but ignore that the concept of the fund pool itself is centralized. The BitVM bridge has improved the security of the chain bridge from the source by decentralizing the fund pool.
So what are the downsides?
However, no plan is perfect and there will always be some unsatisfactory aspects.
Careful friends will find that the BitVM bridge operator prepays funds to users and then reimburses from the public account, which is similar to the form of a fund pool. One pool is a public account (that is, the users real locked assets, responsible for directly reimbursing the operator), and the other pool is a pool formed by operators, which is used to directly advance users withdrawal needs (this pool is virtual and scattered among different operators).
When a user initiates a withdrawal, the funds are directly transferred to the operator, which is equivalent to the operators final funds becoming the funds of the fund pool.
Limited by this fund pool model, for some users who attach great importance to the source of funds, the BitVM bridge cannot actually meet their needs for fund independence.
In order to address this issue and reduce over-reliance on the BitVM bridge, Bitlayer has added the OP-DLC bridge solution, which is similar to the idea of a pipeline to enable user P2P transactions. The security of the OP-DLC bridge relies on fraud proofs and third-party oracles.
What about availability?
The security of the BitVM bridge is beyond doubt, but the usability issue needs to be continuously improved . For example, according to BitVMs expectations, a large number of alliance members need to be online and pre-sign correctly to ensure the correctness of the process, which is actually a challenge.
3. Summary
In terms of architecture, Bitlayers LVM achieves the decoupling of smart contract execution and zero-knowledge proof. This is actually a forward-looking design idea, making it possible for Bitlayer to adapt to various VMs and zero-knowledge provers in the future.
In terms of cross-chain bridge technology selection, Bitlayers BitVM + OP-DLC dual-channel bridge is basically the most secure cross-chain bridge implementation solution for BTC L2 at present (minimizing trust).
Bitlayer has built a cross-chain bridge solution that is relatively both secure and scalable based on BitVM through the integration of technology and engineering. However, this is only a transitional stage and a compromise after weighing security and scalability.
Minimizing trust should be the goal pursued by BTC L2. As BitVM becomes more practical little by little, and as far as I know, it is expected that Bitalyer will have another major breakthrough in the construction of BitVM in about three months. We look forward to Bitlayer becoming the BTC L2 we expect step by step.
refer to:










